Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Paths to Power in Active Directory Part 2: ESC1 – No One, Yet Anyone
This is the second post in this series. Part I can be found here. Planning The Take Over: Identifying the Cracks in the Wall In GOAD (Game of Active Directory), as with real-life engagements, ESC1 is often the first crack in the wall worth checking once AD CS comes into play. It’s not the beginning ...
Continue Reading
Never miss a Professionally Evil update!
Extract Secrets from Multiple Configuration Files Using Vim
You're SSH'd into a compromised Linux server during a penetration test. You've found the ...
Continue Reading
Paths to Power in Active Directory Part 1: How AD CS Misconfigurations Become the Keys to the Kingdom
An Introduction to Active Directory Certificate Services (AD CS) I am still pretty new to ...
Continue Reading
No Broadcast Traffic? No Problem! - NetExec SMB Slinky Module
As pentesters, tools such as Responder and Ntlmrelayx are great tools for capturing hashes or ...
Continue Reading
Annual Pentests Aren't Cutting It Anymore: Why Continuous Testing Beats Scrambling at Renewal Time
Let's be honest about something: if you're still relying on that once-a-year penetration test to ...
Continue Reading
Quantum Leaping Through Data: Preparing for the Quantum Encryption Transition
best practices |
compliance |
risk assessment |
NIST |
CISA
Quantum computing and its implications for cryptography isn't a new discussion. Security ...
Continue Reading
Your Risk Framework Is Broken: The Al Reality Check Every CISO Needs
Every risk management framework in cybersecurity relies on the same fundamental equation: Risk = ...
Continue Reading
Rolling for Resilience Part 2: The Communication Gauntlet
This is the second post in this series addressing my perspective on the current state of ...
Continue Reading
Bypassing Browser PDF Security: Using Embedded JavaScript Forms for Social Engineering
I can say that, since I started my journey at Secure Ideas, I’ve felt extremely fortunate. Not only ...
Continue Reading
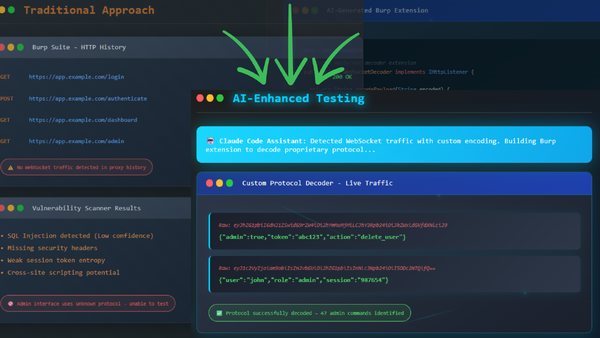
The Real AI Revolution in Penetration Testing
Custom Tooling at Lightning Speed Most cybersecurity professionals hear "AI in penetration testing" ...
Continue Reading
Quick Bites 13 – Network Pentest Restrictions Can Hurt Your Business
Too Many Network Pentest Restrictions Can Hurt Your Business
Continue Reading
But AI Can Give Me the Commands! Why You Still Need to Learn the Linux File System
Linux |
AI |
AI Security
It’s now easier than ever for AI to write your bash scripts or give you the exact command to ...
Continue Reading
Has contents: true
Total pages: 32
Current page: 1








-1.png)