Many organizations do not include phishing in their annual penetration tests, as they believe that most phishing emails will be stopped by their email filtering solutions. Any “phishy” emails that get through will likely be clicked on by their employees but stopped by anti-virus or web filtering controls. These controls are good, but they typically don’t catch everything, especially targeted attacks that use spear phishing.
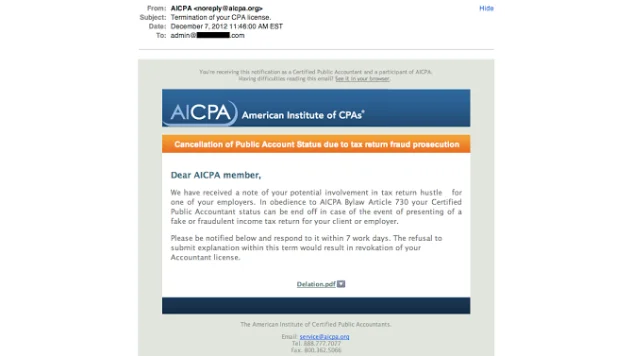
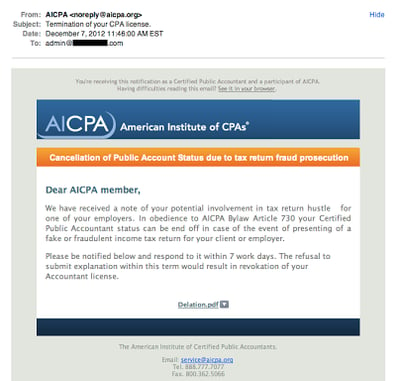
Phishing can be defined as an attempt to obtain sensitive information, such as logon credentials, credit card numbers, and the like, using some form of electronic communication, such as email and social networks, appearing to be from an authentic or trusted entity. Many people can spot a phishing email rather easily, however they are getting more and more difficult to spot. The typical “tell tales” are misspellings, bad grammar, and an over urgency to act. The example below does a good job of masquerading an original email by setting the From email address and the content of the page as being quite believable, unless the recipient is not a CPA. However, you will notice bad grammar and some poor word selections, such as “hustle”, which should raise an eyebrow as to the authenticity.
So let's dig a little deeper into this email by reviewing the raw message. Every email tracks each SMTP server that receives the message for either delivery or forwarding on to the next SMTP server (called relaying). Below we can see that the email never originated from the domain listed in the email address of the sender.
Spear phishing is basically phishing that is focused on a specific target, such as a company, organization, government agency, or some group of individuals, where the attack leverages information about the target to increase the ability for success. These types of attacks may result in fewer victims, but are extremely effective as only a few victims are needed for the attack to be successful. It really only takes one individual to click on a malicious link that provides an attacker an open door to an organization’s internal network.
The first step in a spear phishing attack is to perform reconnaissance on the target organization. The recon should reveal the type of organization it is, identify names of senior management, organizational structure, significant recent or upcoming events, and affiliations (political, religious, charitable, etc.) that the organization or its employees may have. The recon should also include identifying what controls are in place that may prevent a phishing attack, such as web filtering or A/V products, which will be important to know when selecting a payload for the attack. This can be performed by performing some good Google searches, checking blog entries and social networks.
Next is to select the payload that is likely to be the most effective against the target. Not long ago it was easy to bypass A/V with an encoded Metasploit payload, however, these products have improved making this more difficult. If this is the desired payload, then it’s best to obtain the A/V product that the target is using (if discovered during recon), and perform some testing in your own lab environment to see what encoding method works best. The Social Engineering Toolkit (SET) integrates with Metasploit and offers a number of options to create a payload and a listener. One of the best methods for “hooking” a client is to use BeEF, the Browser Exploitation Framework. BeEF does a wonderful job of taking control of the victim’s browser and get a foothold into their internal network, all by using JavaScript, which is rarely blocked. A simple “payload” is to use a link, obfuscated of course, that connects to a server that tracks each connection.
Once the payload is decided upon, a method of delivering the payload must be determined. This can be in the form of an email that appears to have originated internally, such as Human Resources or Corporate Communications. The From and Reply To addresses can be manipulated to appear that the email originated internally. This can still be effective depending on how well an organization filters these types of attacks, and how suspicious the recipients are to these types of emails. However, we have seen both in the industry and first hand how effective spear phishing attacks can be by using email. Once again SET provides a nice feature in handling a mass mailing of phishing emails, making this part of the attack rather easy. Another method is to leverage the inherent level of trust that people have with social networks. Setting up a fake account on a social network, masquerading as an employee, an ex-employee, or someone interested in being an employee, can typically lead to establishing connections with employees of the organization, and quickly gaining their trust enough to have them click on a malicious link or open a malicious PDF or other attachment. Be aware that setting up fake accounts violates most social networks’ terms and conditions.
Now that the recon is completed, and a payload and delivery method have been decided upon, it is time to establish a pretext or story for the communication to the target. The context needs to be believable, something that the recipients can relate to and will be enticed to act upon by clicking on the link or attachment. This is where the earlier recon will help in identifying a pretext that will be the most effective. Depending upon the payload and the delivery method, the communication to the target is likely to have two parts. The first being the communication that will lead the target to take action, enticing them to act, and thus delivering the malicious payload. The second communication is delivered with the payload itself, such as the context of a malicious PDF that includes a meterpreter backdoor, or the context of a web page with a BeEF hook to keep the victim on the page as long as possible. Good examples of this are sending a new corporate policy as a PDF, or sending a company survey page, hosted by the attacker, for employees to fill out. One of the best steps in making the context believable is to ensure every word is spelled correctly and that the grammar is spot on.
The last step is to identify a way for capturing the results, which will depend greatly on the payload and delivery method used. Almost all payloads will result in connecting back to the attack server, whether that is with establishing a meterpreter session, being hooked with BeEF, or simply linking to a web site. All of these methods provide a way to view the results of how many times the payload is executed, thus how successful the attack is.
Many organizations do not know how vulnerable they are to these types of attacks and the risks are typically based on assumptions. There are three questions that an organization’s management should be asking, and wanting answers to, when it comes to phishing and spear phishing attacks:
- How vulnerable are employees to these types of attacks?
- How effective is the security awareness program in helping employees identify phishing and spear phishing attacks?
- What is the potential impact if an attack is successful?
Performing phishing and spear phishing tests can help answer these important questions, and help lead management to establish or enhance corporate policies, user awareness training, and additional technical controls. Performing this testing on a periodic basis provides management with results that identify trends and help make further adjustments, indicating a return on investment over time, determining what works, and what doesn’t. For many organizations, performing this type of testing is not in their area of expertise, or they simply do not have the time. This is where a service, such a MySecurityScanner (MSS) can be helpful. MSS is a subscription-based service that offers three types of vulnerability assessments: network infrastructure, web applications, and security awareness. It is the security awareness service that includes phishing assessments, using social engineering methods that can answer the questions listed above. Since it is a subscription-based service, it can be performed on a periodic basis that best aligns with the needs of the organization, either scheduled, or as needed.
Tony DeLaGrange is a Senior Security Consultant with Secure Ideas. If you are in need of a penetration test or other security consulting services you can contact him at tony@secureideas.com or visit the Secure Ideas – Professionally Evil site for services provided.