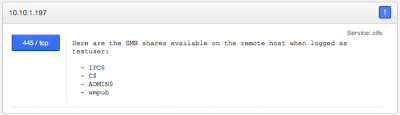
One of the common vulnerabilities we find when performing internal network penetration testing is sensitive data on open SMB file shares. Now, by “open” I am including both unauthenticated as well as file shares that allow any authenticated user. It certainly makes sense for organizations to have file shares that are accessible to all employees for non-sensitive information, however, this has to be monitored as users are not always as careful with sensitive information as they should be. For example, I remember performing an internal network penetration test for an organization that we had previously tested a year before. We were using Nessus to scan the systems in scope of the test and discovered, as the year prior, that many open file shares existed. When discussing this with one of the employees on the Information Security team, I was informed that they were unable to fix many of the issues identified in the previous penetration test because the report was considered too sensitive to share. The ironic part is, one of the open shares we discovered had the previous year’s penetration testing report on it, accessible to anyone to any authenticated user on their network.
There are many tools that provide the ability to identify open SMB file shares. The default configuration of Nessus will identify SMB file shares that do not require any authentication.
By providing Nessus with a valid domain user account, it can search for file shares that are accessible to any authenticated user. The account should be one that is used specifically to perform the scanning, and should be setup as a typical new user account, but without any departmental specific access.
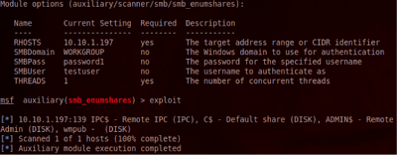
Metaploit has a module that can be utilized for scanning SMB file shares. The module is auxiliary/scanner/smb/smb_enumshares, which also supports searching SMB file shares with or without user account credentials. In the example below, I have set RHOSTS to the IP address of my test server, SMBUser is the user name for my test account, and SMBPass is the password for that account.
set RHOSTS 10.10.1.197
set SMBUser testuser
set SMBPass password1
Once everything is set, the exploit command starts off the module and searches for open SMB file shares, as shown below.
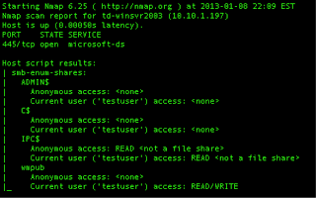
If you are a big fan of Nmap, as I am, you can also use it to search for open SMB file shares by using the smb-enum-shares.nse nmap script. To perform the scan with user credentials, just add the smbuser and
smbpass script arguments.
smbpass script arguments.
nmap –script smb-enum-shares 10.10.1.197 -p445 –script-args
smbuser=testuser,smbpass=password1
The output from Nmap reveals all of the enumerated SMB file shares for this host, but also provides something a bit more – the access to the file share.
This is why Nmap is my favorite tool to find open SMB file shares. Finding a SMB file share with READ access
gives us the opportunity to search for sensitive information. However, having WRITE access to an openly accessible SMB file share is a great way for attackers to store and distribute malware.
gives us the opportunity to search for sensitive information. However, having WRITE access to an openly accessible SMB file share is a great way for attackers to store and distribute malware.
Unfortunately, the script doesn’t support a Grepable format that includes the actual SMB share names and access. However, that won’t stop us as we can use grep to extract what we need out of the normal format. The command line below will extract the SMB file shares with READ access, accessible with our testuser account, excluding SMB shares that are not actually file shares.
grep
-v “<not a file share>” smb-shares.nmap | grep -B 2 “(‘testuser’)
access: READ”
To extract the SMB shares with anonymous access just needs a minor change.
grep
-v “<not a file share>” smb-shares.nmap | grep -B 2 “Annonymous
access: READ”
Looking for open SMB file shares is something that every organization should be doing on a regular basis. Each file share should be restricted based on least privilege access, meaning only those that need access have it, and only have the level of access required (e.g. Read vs. Write). File shares that need to be accessible to the entire organization should have a default access of READ, and require users to be authenticated, using groups to permit and restrict WRITE access. Once a baseline is established of all the file shares in the organization, it’s easier to validate subsequent scans to help identify new file shares that are not properly restricted.
Once a list of open SMB file shares is identified, it’s then possible to utilize tools such as OpenDLP or Cornell’s Spider to search for information that is considered sensitive. OpenDLP is available on Google Code at http//code.google.com/p/opendlp and Cornell’s Spider tool can be found at http://www2.cit.cornell.edu/security/tools/spider-linux.html.
Tony DeLaGrange is a Senior Security Consultant with Secure Ideas. If you are in need of a penetration test or other security consulting services you can contact him at tony@secureideas.com or visit the Secure Ideas – Professionally Evil site for services provided.