There are multiple ways to test a mobile application. One technique, that I won’t be covering in this post, is to hook up a proxy server for your device and intercept the HTTP(s) traffic that is passed around. Another way, which is the focus of this article, is to capture all of the traffic between the device and the server. This method not only captures HTTP traffic, but also allows inspecting other protocols that the application may be using. This is ideal when the application uses raw sockets vs generic HTTP requests.
When testing a mobile application, on a physical device, there are a things that make it easier. The first step is to have a dedicated wireless router or access point specifically for the mobile device. For example, I have a Linksys router that is used only for mobile device testing. The second step is to intercept the traffic from the wireless device to the internet. This can be done by placing a tap between the wireless router and the other routers and connecting your computer to the Tap.
I choose to use the Throwing Star LAN Tap Pro from Great Scott Gadgets (http://greatscottgadgets.com/throwingstar/). There is also a non-pro version, but dust off your soldering skills to put it together. The setup is really easy. The following steps are used to do the hardware setup:
* Wire the Wireless Router/Access Point to the Throwing Star LAN Tap
* Wire the Throwing Star LAN Tap to the existing infrastructure
* Wire your computer to the Throwing Star LAN Tap on the interception port
The following image shows the LAN Tap wired up:
Now that we are set up to listen in on the traffic, it is time to fire up a packet capture program. I use WireShark, but you could use a different program if you prefer. You can get WireShark from http://www.wireshark.org/. Setting up Wireshark is pretty quick and easy.
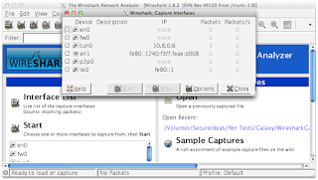
Once you open WireShark, Click on Capture…Interfaces to select an interface (seen below):
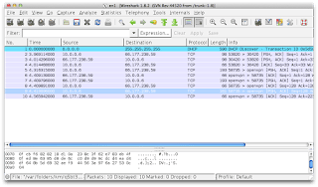
After Selecting an interface, click the start button to start capturing traffic. The following image shows an example of WireShark capturing packets.
Now that you have packets, you can start to analyze them. The benefit of capturing this level of detail when testing a mobile application is that it allows you to see more than just the standard HTTP traffic. It is not uncommon for developers to use direct connections rather than going through the HTTP Protocol. This technique allows you to view any other connections that the application may be making that a tool such as Burp would not identify.
I recommend everyone that is testing mobile applications to use this technique to ensure they are not missing any connections the application makes.
Want to know more about mobile application penetration testing? Kevin Johnson and James Jardine will be teaching “Assessing and Exploiting Mobile Applications with OWASP Mobisec” at Blackhat USA 2013. There are two sessions running and this is going to be an excellent course filled with hands-on labs. For more information: http://www.blackhat.com/us-13/training/assessing-and-exploiting-mobile-applications-with-owasp-mobisec.html
James Jardine is a Principal Security Consultant with Secure Ideas.
If you are in need of a penetration test or other security consulting services you can contact him at james@secureideas.com or visit the Secure Ideas – Professionally Evil site for services provided.