If you haven’t seen it in the news, you must not have any technology close by. That is right.. another story about heartbleed. But this is different. The goal is to discuss the patching of this nasty bug so that consumers and companies are properly protected. We see websites telling us they have applied patches and we need to reset our passwords, but is that all that needs to be done?
For the business.. Have you patched the openSSL version that you are using? That is the first step in remediating this issue. You would want to plug the hole in your boat before bailing water, otherwise you are just continuing to be vulnerable. This doesn’t just go for websites, although it may seem like that at times. Any application that uses a vulnerable version of the openSSL package is also at risk. Make sure you have a way to patch those as well. For example, VPN systems and instant messaging clients. Did you look at your patch management or infrastructure management systems?
Once you have patched, it is time to think about issuing a new certificate for your secure connection. It has been shown by CloudFare (http://blog.cloudflare.com/answering-the-critical-question-can-you-get-private-ssl-keys-using-heartbleed) that it is possible to retrieve the private key used for the secure connection. With this private key, it is possible for the bad guys to intercept and decrypt the traffic (snoop on sensitive information). This is an important step to take because there really is no good way to know if the private key has been compromised, and if it is, just patching openSSL isn’t going to solve the problem.
After issuing the new certificate, it is time to think about the user information. Do we need to force a password reset, just in case? What about other sensitive information that may be held in memory on the server. This is a good time to think about how you handle sensitive information within your application. Do you store it in strings, which are difficult to manage their lifecycle in many languages? For example, in .Net, since the string object is stored on the heap it is managed by garbage collection. This makes it difficult to truly control how long it lives in memory. A better option is using arrays if possible because they are easier to clear out of memory, or SecureString if you can do that safely.
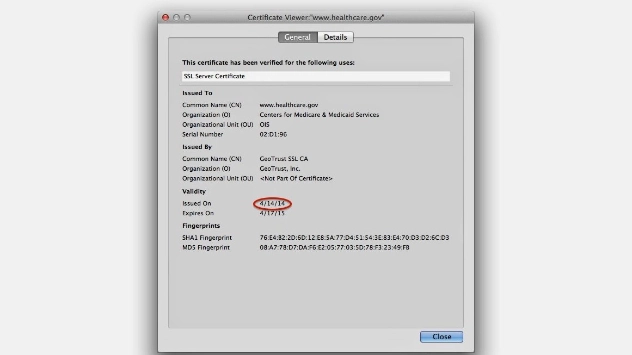
For the consumer…There really isn’t much we can do about what data may have been compromised. Many sites are very open about being vulnerable to the heartbleed bug and have posted to reset your password. If this is the case for a site that you use, also check the certificate to see if it has been updated. In Firefox you can just click the lock icon in the address bar and click “more information” and then “view certificate”. If the certificate was issued before april of 2014, then be a little more cautious that the site hasn’t fully eradicated the problem. The following image shows a certificates details:
The next step is to then change your password just in case it was compromised. It is better to be safe than sorry. It may seem like we are changing passwords a lot lately, but as we all know the password system is not the best so we just have to make due.
It is unfortunate that such a bug existed, but doing some simple steps we can bounce back and regain the trust we need in all the sites we use. There will always be some amount of risk with everything we do on the internet.
James Jardine is a Principal Security Consultant at Secure Ideas. If you are in need of a penetration test or other security consulting services you can contact him at james@secureideas.com, @JardineSoftware, or visit the Secure Ideas – Professionally Evil site for services provided.