Imagine going in to do an incident response at a fairly large customer that has no visibility within their firewalls, no intrusion detection, no sense of inventory, because they had no ability to run even the most basic of vulnerability scans across their network.
If I just described something that sounds a little scarily like where you work, listen up: the fact of the matter is, if you can’t answer basic questions about your network, about what makes it move data from left to right, top to bottom: about how your company takes keyboard clicks at one end of the value chain and turns them into money at the other, then your company has very large problems.
When you call an incident, the incident response team is going to find more than one incident in progress.
What you can do, if you find yourself working at such a company, is not accept it. And yes, we understand that there are always many political reasons, with money heading the list, why people do not have to do this work. But not doing the work creates an existential threat to the company. This isn’t a joke.
You simply must understand what normal looks like. If you don’t, no one can look at what you have and get you back to normal.
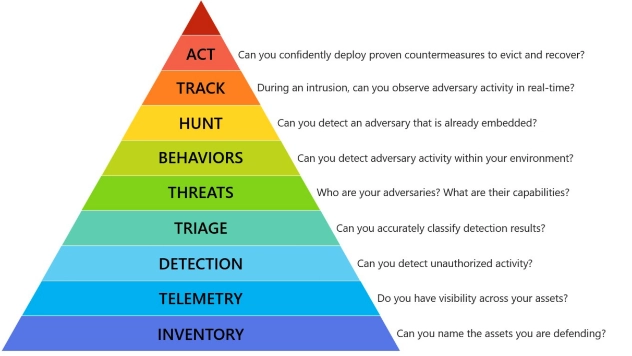
Matt Swann, a Principal Engineering Manager at Microsoft, has come up with his version of Maslow’s Hierarchy of Incident Response Capabilities, which begins with Inventory and Telemetry, or “What do you have” and “What can you see?”
It’s the illustration shown in this post, and while it is only at version 0.3, it’s the best I’ve seen yet to describe what we face every day.
Remember: the bottom two things – the foundation of the pyramid – are Inventory and Telemetry. I get asked all the time “How can I make my company better prepared for an incident?” I cannot emphasize enough the importance of these two things as preparation for that day.
It’s almost as if I’m saying that buying a threat feed just isn’t as important as understanding and being able to see inside your environment.
If you do nothing else in your company this coming year, work on getting an inventory.
You can get a good idea of what you have by running vulnerability assessment tools – a classic neat exercise remains taking diagrams of your subnets and then scanning those same subnets and seeing what is different. And then working to understand why.
The next thing is getting visibility into your traffic. We speak with customers literally every day about visibility, and I think maybe it is because so many people are selling ads for “threat intelligence,” that they seem terrified to do something and get started lest they do the wrong thing, so they do nothing, but for some reason, people seem hesitant to actually start putting tools on their network to see what is out there. Security Onion is a wonderful set of tools that can get you started at absolutely no cost, and you will soon start to get visibility into what is talking to whom, when, and – with a little finesse, you can infer why. I say again: it is free.
I showed this post to Matt, who commented:
“Another angle on this is to take an “assume breach” perspective: everyone is going to experience a breach, the question is “when” not “if”. If you haven’t built any of these capabilities before the breach, then afterwards you’ll have to bring in IR consultants to build all of these capabilities from scratch.
“It’s far better to build these capabilities now so that you can detect and respond to the breach in progress to limit the impact to your business.”
I could not agree more.
“Another angle is around “cyber insurance” — I would not be surprised to see insurance providers evaluating these capabilities within an organization to determine pricing and exposure.”
Matt said it best – these are the “Minimum requirements for me to help you” -> you must be this tall/have these capabilities for me to get you up the pyramid.”
That’s hard to if you’re going to spend the first four hours of our time together running through our inventory exercises.
To make one thing absolutely clear: if you as a company are unable to handle the bottom two layers of Matt’s pyramid – and I mean, absolutely understand both layers for your entire organization – not partial, not “except for our cloud services” or “except for our China operations” but everything – then when you get hit, your company faces a crisis that is expensive, reputation damaging, and absolutely, entirely avoidable.