Often, one of the main goals of a pen tester is to get Domain Admin (DA) rights in a client’s Windows network. But why do we want to get that level of access? For some, it may just be the satisfaction of navigating far enough to compromise the DA account. But, in reality, gaining DA is a just means of obtaining unfettered access within the network. You can grant yourself access to any sensitive materials or data. That is the true risk to the client and something we should not forget.
As companies continue to enhance their security posture, gaining DA access will take more and more effort, eventually even more than we have allotted for the test. Maybe DA’s are restricted to Domain Controllers and special, controlled devices (i.e. Microsoft’s Privileged Access Workstation). At that point, it will become more important to look for other accounts that may have some of the same abilities, just in different ways. One option is to look to see which accounts have been delegated rights within the directory. If DAs are restricted, there is a good chance that other accounts have the ability to modify user accounts or group memberships. Knowing who has the ability to modify which Active Directory objects is essential for both red and blue teams.
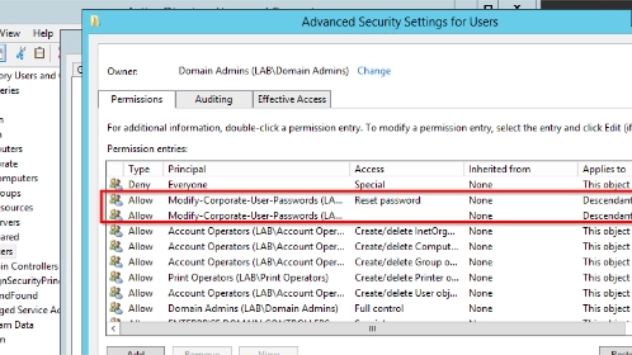
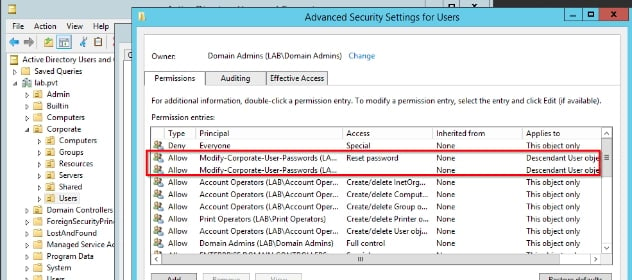
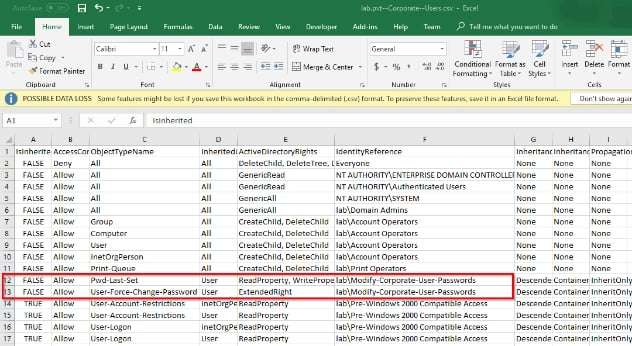
Using the GUI tools is impractical for gathering this information. There is nothing in the default views to indicate that permissions on the Organizational Unit (OU), or objects in the OU, have been modified from their parent objects. The Advanced Security Properties of every object would have to be individually opened and reviewed.
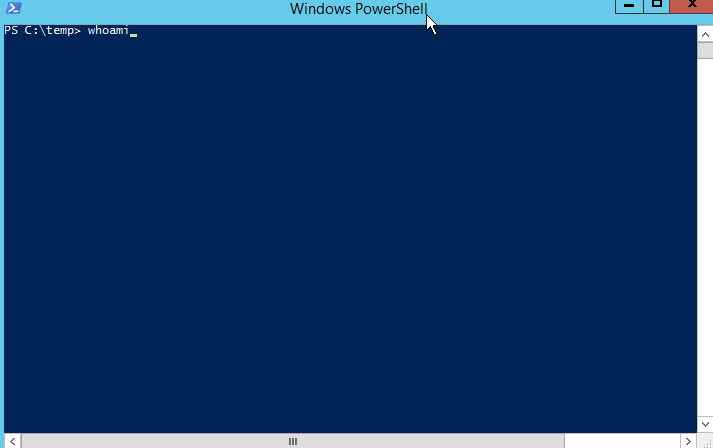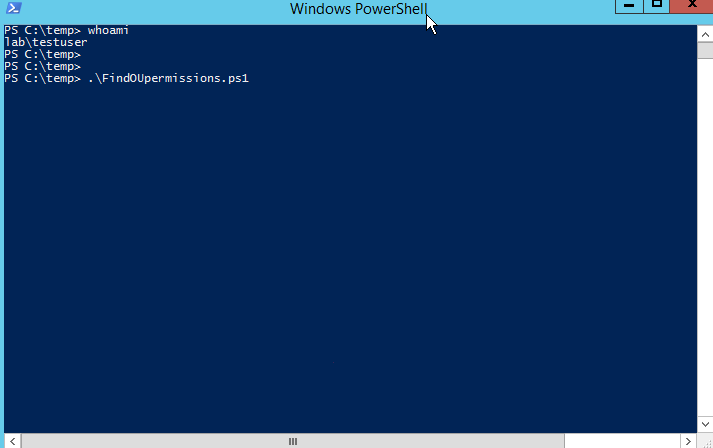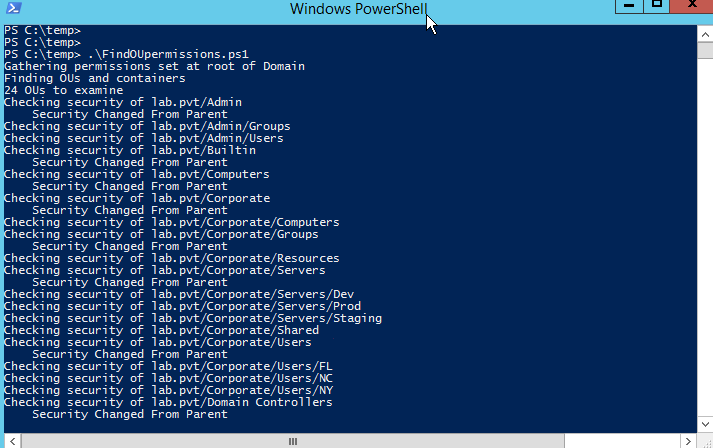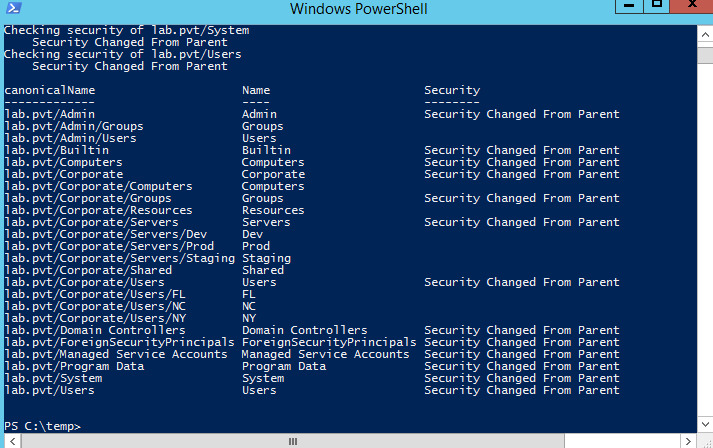
Even for small directories, this is too time consuming to be practical. Therefore, I wrote a couple of PowerShell scripts that find all of the OUs (and top-level containers), evaluate the permissions on the OU compared to the parent object, and export a list of the permissions when they are different. Both scripts require RSAT to be installed on the device running the scripts.
The first script, FindOUpermissions.ps1, is meant to be run from a windows system that is a member of the Domain that is being queried. It is very fast and doesn’t require any parameters to run.
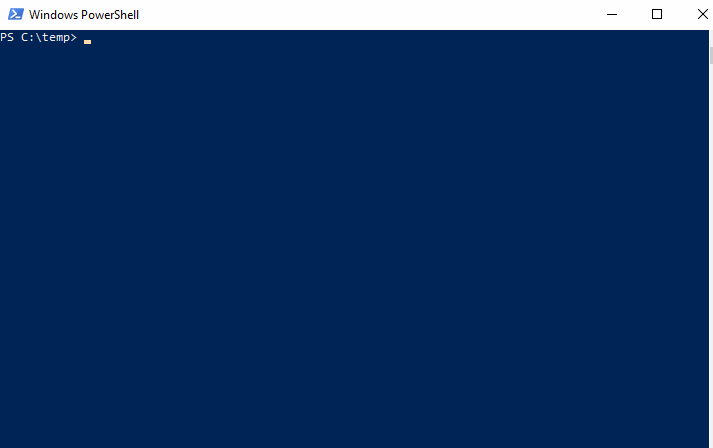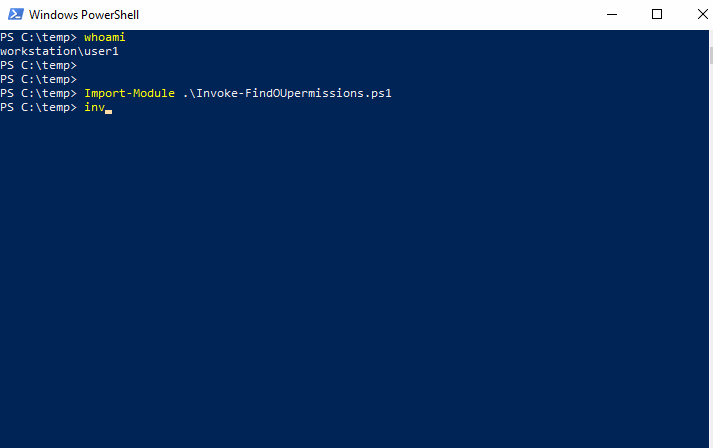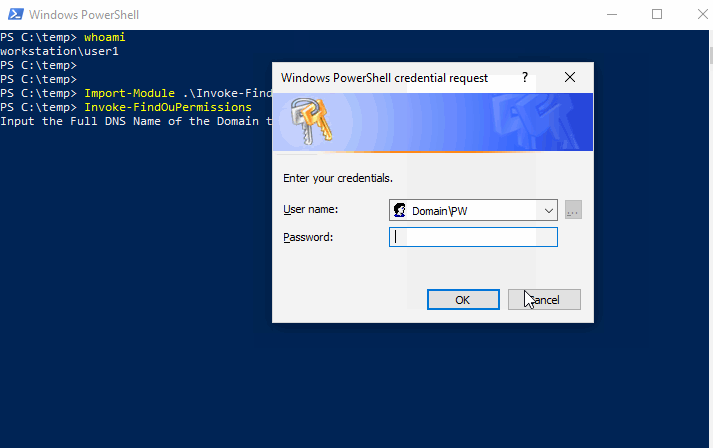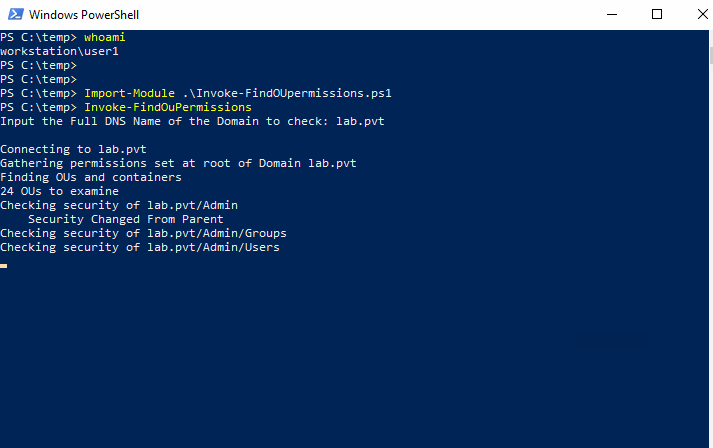
The second script, Invoke-FindOUpermissions.ps1, is much slower but can be run from a windows system that is not a member of the Domain or Forest being queried.
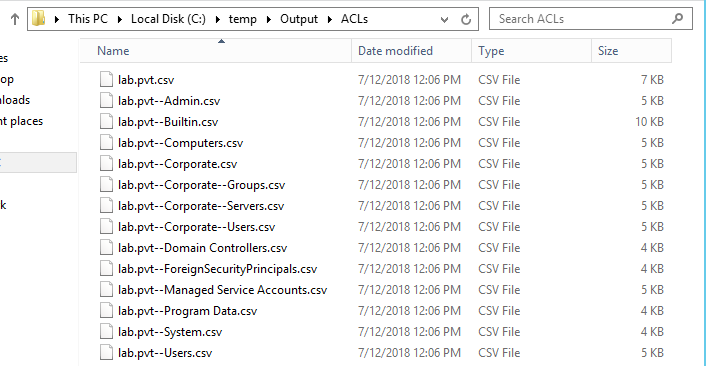
When they complete, they export the permissions in CSV files.
Both are available as Github Gists:
- FindOUpermissions.ps1 – https://gist.github.com/neKuehn/d4d922066744b406816fe66714e0c66a
- Invoke-FindOUpermissions.ps1 – https://gist.github.com/neKuehn/61f70b2d54a4344b5638c0625e2f8ca6
If you’re interested in looking into OU permissions, give them a try. I hope these will be useful both to red teams and blue teams. These are not the only method that could be used to gather and report on the information, but they are one way and, being PowerShell scripts, they can easily be modified to return the data in different formats.