Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
When Security Fails: What The DeepSeek Incident Can Teach Us About AI Security
The advent of generative AI - particularly Large Language Models (LLMs) - marks a paradigm shift in how we must approach security and privacy. As security professionals, we can leverage AI to enhance and augment our defenses, but we must also recognize the new attack surfaces that AI introduces. ...
Continue Reading
Never miss a Professionally Evil update!
Prompt Injection
information security |
AI |
machine learning |
artificial intelligence |
cyber security |
Prompt Engineering |
AI Security |
Prompt Injection |
ML
What is Prompt Injection?
Continue Reading
Taming the Enterprise AI Beast Webcast
As artificial intelligence (AI) continues to become more and more integral to business operations, ...
Continue Reading
Encrypting Data on the Steam Deck with Plasma Vaults
encryption |
Gaming |
Privacy |
Steam Deck
In my previous post about the Steam Deck we discussed some of the privacy and security concerns ...
Continue Reading
Sailing into the Unique Security Risks of AI Systems Part 1
As we venture further into the vast ocean of Artificial Intelligence (AI) - employing it to ...
Continue Reading
Steam Deck Privacy and Security
Like any portable computing device, there are going to be questions about privacy and security. The ...
Continue Reading
Digging Between the Couch Cushions - CouchDB CVE-2021-38295 Breakdown
Vulnerability |
developers |
security |
open source |
information security |
application security |
hacking
Introduction In this blog post we’re going to take a look at the recent CouchDB vulnerability, ...
Continue Reading
Game Hacking Part 1 - Equipping Your Loadout
Why Bother with Video Game Security? Video games are more than just entertainment. Gaming is a ...
Continue Reading
Kubernetes Security - A Useful Bash One-Liner
Whether you’re an administrator, pentester, devop engineer, programmer, or some other IT person, ...
Continue Reading
It's Okay, We're All On the SameSite
With Google’s recent announcement that all cookies without a SameSite flag will be treated as ...
Continue Reading
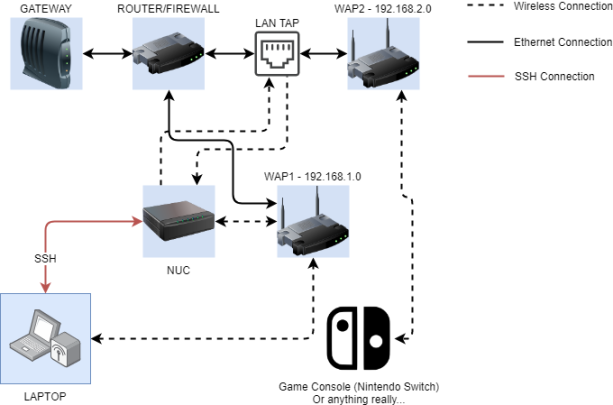
Game Console Hacking: Part 1 Lab Setup
This is the first in a series of blog posts on my journey through video game hacking and security. ...
Continue Reading
A Container Hacker’s Guide to Living Off of the Land
hacking |
container hacking |
container security |
containerization |
pentesting |
living off the land
Sometimes as a pentester you find yourself in tricky situations. Depending on the type of ...
Continue Reading
Has contents: true
Total pages: 2
Current page: 1