Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Place Your Right Hand On This Glass
One of the hassles of the Yahoo! breach was clearly the coming-home-to-roost quality of the ...
Continue Reading
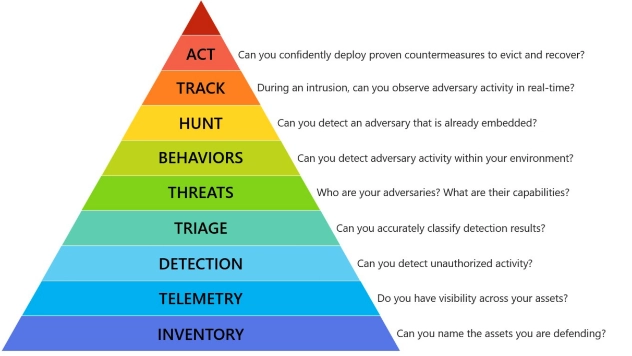
You Must Be This Tall
Imagine going in to do an incident response at a fairly large customer that has no visibility ...
Continue Reading
Statement by Nick Selby on Bishop Fox / Muddy Waters Report
FOR IMMEDIATE RELEASE: Statement by Secure Ideas Response Team Director Nick Selby on the Report ...
Continue Reading
SQLMap Beginnings: What and How
Testing web based applications is not only fun but is often multi-faceted and challenging. Often ...
Continue Reading
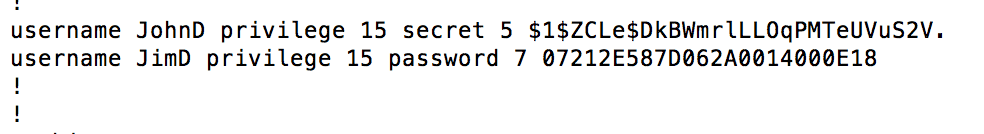
Reversing Type 7 Cisco Passwords
While working on a recent pen test, I came across a few Cisco routers sitting on an internal ...
Continue Reading
SamuraiWTF 3.2 RELEASED!
We are really excited to announce that SamuraiWTF 3.2 is now available publicly. This release is ...
Continue Reading
Patching binaries with Backdoor Factory
When was the last time you downloaded a binary file from the Internet or grabbed one off of a ...
Continue Reading
Installing Splunk: First stop on the road to log analysis
First thing’s first: What is Splunk and why do I want or need it? The short is answer is Splunk is ...
Continue Reading
Beware of Holiday Scams
It is that time of year and we need to be ready for the fraudsters to be out in full effect. The ...
Continue Reading
SQLite: the good, the bad, the embedded database
SQLite is an embedded, open-source, lightweight SQL database engine. The C based library is ...
Continue Reading
Thumb Drives.. Can you tell the difference?
During a physical penetration test, it is not uncommon for the tester (attacker) to drop usb thumb ...
Continue Reading
Has contents: true
Total pages: 7
Current page: 2