Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Logging Like a Lumber Jack
Turn on any news outlet or visit any news site and you will most likely see an announcement of yet ...
Continue Reading
Policy Gap Analysis: Filling the Gaps
In today’s world, something never seems to be true unless it is written down, and even then it is a ...
Continue Reading
New Data Security Breach Laws in Florida
Since many organizations are collecting what many would consider personal, non-public, information, ...
Continue Reading
What Do You Expect From A PenTest?
There are many reasons that a company has a penetration test performed. Maybe it is due to ...
Continue Reading
Ebay Falls Victim to Breach: Source Forge Updates Password Storage
It was just recently announced that eBay suffered a breach that led to the compromise of user ...
Continue Reading
Webcast: Comprehensive testing: Red and Blue Make Purple
Secure Ideas is excited to announce a webcast scheduled for May 13th, 2014 on the topic of Purple ...
Continue Reading
Purple Teaming for Success
You know what blue teams and red teams are. Red is our attack side, or the adversaries, and Blue is ...
Continue Reading
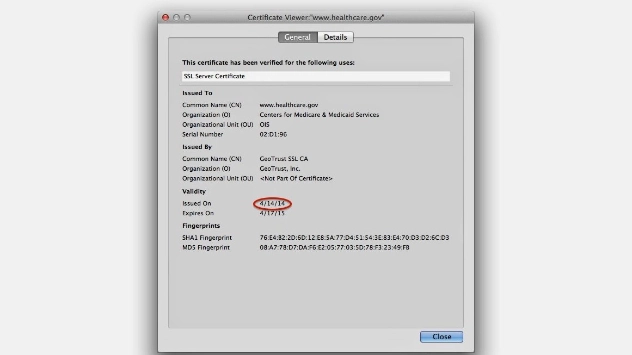
Heartbleed: Complete Heart Surgery
If you haven’t seen it in the news, you must not have any technology close by. That is right.. ...
Continue Reading
Windows XP: Eol, What you need to know
Last week Windows XP finally reached its end of life. The operating system was released back in ...
Continue Reading
Auto-Updating Devices: How to Test?
Everyday we see new technology and devices in our everyday lives that are connected to the ...
Continue Reading
Oversharing: Who Has Access?
What types of information do you copy to a shared folder? Who has access to the share? This can be ...
Continue Reading
Has contents: true
Total pages: 7
Current page: 3