The goal of this article is to walk through how to set up a Windows host to allow multiple remote desktop (RDP) sessions. This can be useful to consider, especially when viewed from a penetration testing frame of reference.
The general background to this scenario is that when working on an engagement, typically an internal network test, there are times when credentials are acquired which allow us to RDP into a server or workstation within the domain. Occasionally, this is a high value target, and other times it’s simply a staging platform that we can work from.
Since this type of testing will often involve more than one consultant, it’s often useful to leverage this newfound access by adjusting the number of connections allowed onto the workstation or server. Having a device where we can each do a variety of tasks can be noisy at times, but it also allows us to coordinate efforts and review results more easily as we seek to expand our access and influence within the domain. Due to time constraints, which are a normal part of testing, stealth is not the main focus here.
With that to help set the stage for what we’re doing and how it can be useful, this is a fairly straightforward adjustment, provided you know where to look for the settings.
In order to configure a Windows system to allow multiple RDP sessions, you can refer to the following steps:
- Either click on the Windows Start menu (or use win+R) to open up a Run window
- Next, type in, gpedit.msc , and hit Enter
3. Navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections
4. Disable the single session setting: Restrict Remote Desktop Services users to a single Remote Desktop Services session
-1.webp?width=592&height=330&name=pasted%20image%200%20(1)-1.webp)
5. Finally, enable the Limit number of connections setting and then change the RD Maximum Connections allowed to the number of connections you need for that device.
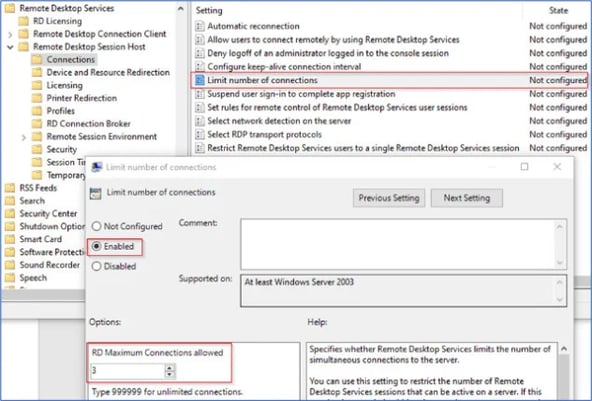
In this particular example, we’ve adjusted the maximum number of RDP connections from 1 to 3. It should be noted that if this is being done on a customer device, rather than something like a virtual device your team joined to their domain (which will be removed when your testing is complete), then these changes need to be reverted to their original setting at the end of the engagement.
Hopefully this has been an interesting insight into a useful RDP setting. If you’re interested in security fundamentals, we have a Professionally Evil Fundamentals Youtube channel that covers a variety of technology topics. Finally, if you’re looking for a penetration test, training for your organization, or just have general security questions please Contact Us.


