Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Twelve Days of ZAPmas - Day 2 - The Edge of Tomorrow
Day 2 - The Edge of Tomorrow - Replaying and Tampering with Requests Fuzzing and tampering are like ...
Continue Reading
Twelve Days of ZAPmas - Day 1 - Setting Up ZAP
This holiday season, I’m going to run down some of the ins and outs of working with OWASP Zed ...
Continue Reading
Quick Bites Ep 6 - Good Hygiene is IMPORTANT, PEOPLE!
Guidance |
best practices |
Quick Bites |
Cyber |
Hygiene |
CIS Top 18 |
Blue Team
So, I just missed a week of work because of the flu (it wasn’t COVID, I got tested). The flu SUCKS. ...
Continue Reading
How to iterate through advfirewall rules
Training |
professionally evil |
Secure Ideas |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
powershell |
firewall rules
There are several ways to pull firewall information from a Windows system. Today we will leverage ...
Continue Reading
Introduction to Writing Nmap Scripting Engine (NSE) Scripts
NMAP |
programming |
NSE
One thing I notice a lot of people are missing in their skill set as security professionals is the ...
Continue Reading
Quick Bites Ep 5 - The Call Is Coming From INSIDE THE HOUSE
hacking |
Quick Bites |
Insider Threat |
Attacks |
Halloween
Man, I’ll be honest - I’m super excited to be doing a Halloween-themed blog post this year. So, ...
Continue Reading
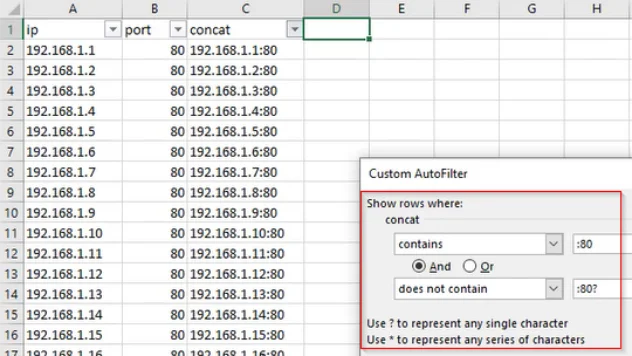
Working With Data: IP and Port Filtering
Training |
professionally evil |
Secure Ideas |
technology tips and tricks |
sysadmin |
data |
data manipulation |
excel |
spreadsheet |
filtering
During our day-to-day work, there’s a lot of data that we interact with. In order to make good use ...
Continue Reading
Coming Soon - Twelve Days of ZAPmas
In December of 2018, I published a twelve-day series of cross-site scripting tips, tricks, and ...
Continue Reading
Nmap vs. Masscan
hacking |
NMAP |
port scanning |
masscan |
host discovery
If you are in IT, chances are you have at least heard of Nmap and Masscan. Both are free and ...
Continue Reading
Quick Bites Ep 4 - Let's Talk About SSRF, Baby!
Let’s talk about you and (application) secur-i-ty! Let’s talk about all the good things and the bad ...
Continue Reading
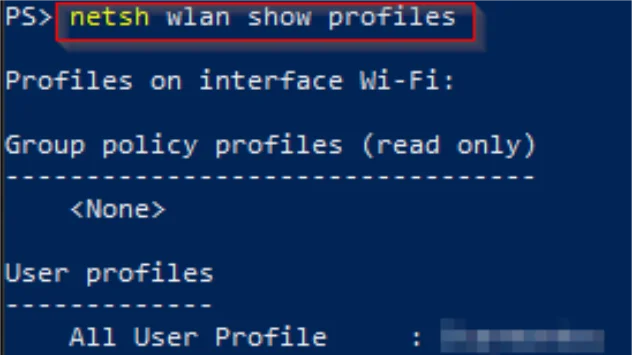
View Wireless Profile Password Information Using PowerShell or CMD
Training |
professionally evil |
Secure Ideas |
hacking |
Windows |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
wireless |
wifi |
wifi password |
powershell |
wireless profile
There are a couple different ways for you to access your Windows wireless password information. If ...
Continue Reading
Has contents: true
Total pages: 39
Current page: 10