Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
10 Tips for Engaging a Security Services Vendor
The Information Security market brought in an estimated $167 billion in 2019 and that’s expected to ...
Continue Reading
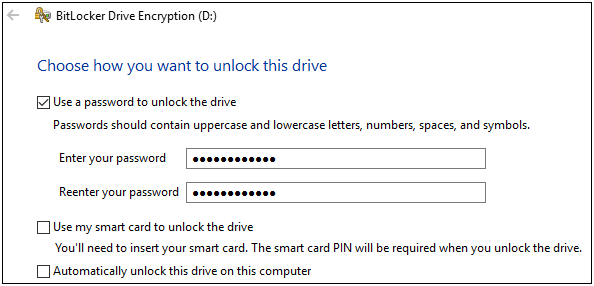
File Encryption Using VHD and BitLocker
encryption |
Windows |
BitLocker |
VHD
When I was thinking of topics to write about, the idea of protecting the data we work with came to ...
Continue Reading
Automating Red Team Homelabs: Part 2 – Build, Pentest, Destroy, and Repeat
pentesting |
automation |
API |
dev ops |
home lab
As of 2019-05-14 the Funny Stories section has been updated. Now that we understand what the goal ...
Continue Reading
Post-Quantum Cryptography Series
Perhaps you have heard of quantum key distribution, or perhaps you are curious as to what quantum ...
Continue Reading
Welcome to the New Secureideas.com
We are excited to announce the launch of the new Secure Ideas website. It is located at the same ...
Continue Reading
That looks ODD Securing your workspace
When you look at “security” and the big picture, it always seems to come down to the decisions made ...
Continue Reading
Better API Penetration Testing with Postman – Part 3
In Part 1 of this series, we got started with Postman and generally creating collections and ...
Continue Reading
We take security seriously and other trite statements
Earlier this week, Secure Ideas sent an initial notification regarding an incident targeting us ...
Continue Reading
Better API Penetration Testing with Postman – Part 2
In Part 1 of this series, I walked through an introduction to Postman, a popular tool for API ...
Continue Reading
Security Misconfigurations
The configuration of web and application servers is a very important aspect of web applications. ...
Continue Reading
Better API Penetration Testing with Postman - Part 1
This is the first of a multi-part series on testing with Postman. I originally planned for it to be ...
Continue Reading
Has contents: true
Total pages: 39
Current page: 18