Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Three C-Words of Web App Security: Part 2 – CSRF
This is the second in a three-part series, Three C-Words of Web Application Security. I wrote a ...
Continue Reading
SamuraiWTF 4.0 Finally Released
In February of this year, Mic posted a blog discussing the future of SamuraiWTF (link provided if ...
Continue Reading
Silencing Firefox's Chattiness for Web App Testing
Firefox is one chatty browser! Even if you don’t actually use it for anything, it’s constantly ...
Continue Reading
Not Just Another Notch in Your Belt: Organizational Challenges of PCI Compliance
As an account manager in the world of security, I am constantly confronted with questions ...
Continue Reading
Gosh Darn Policy Requirements
The Internet was built to be a platform to share information remotely. Since it was created, ...
Continue Reading
A Brief Introduction to MFA
If you are reading this, then you are becoming a cybersecurity geek, or you already are one and you ...
Continue Reading
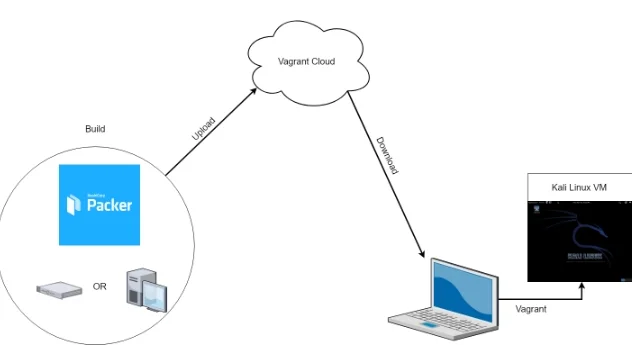
Automating Red Team Homelabs: Part 1 - Kali Automation
Part 2: /2019/05/automating-red-team-homelabs-part-2-build-pentest-destroy-and-repeat.html Homelab ...
Continue Reading
Still SMiShing You - SMS Scams.
Have you ever gotten a strange text message on your phone that you don’t recognize? Well, be ...
Continue Reading
Preventive Security for You
As you go through everyday life, how do you think about your own security? Are you the type of ...
Continue Reading
Security on the Go!
The use of mobile devices is steadily growing. With this increase comes the need for the users to ...
Continue Reading
Introduction to Wireless Security with Aircrack-ng
Today we’re going to walk through a few WiFi testing examples using Aircrack-ng, which is a suite ...
Continue Reading
Has contents: true
Total pages: 40
Current page: 21