Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Xbox One - Capturing the Configuration Traffic
One of the fun things about working at Secure Ideas are the conversations that we have about ...
Continue Reading
Target Security Breached: What You Need to Know
All it takes is one big nasty security breach and the whole world will be watching you through a ...
Continue Reading
Password Sharing Across Accounts
Over the past few years we have seen a large number of databases get compromised leading to the ...
Continue Reading
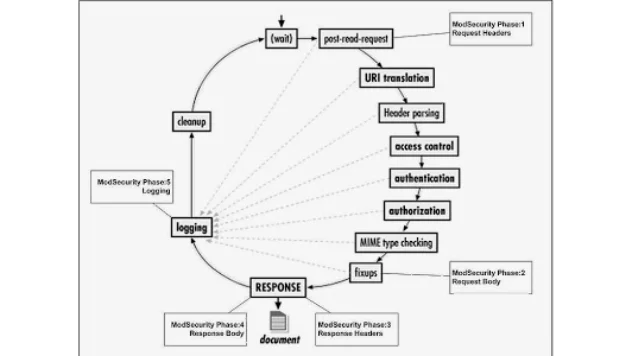
MIRcon 2013 - Analyzing Web Attacks with ModSecurity
Last week I was able speak at MIRcon 2013 about how to use ModSecurity to discover attack activity ...
Continue Reading
Secure Coding for Web Developers Class in Denver
Secure Ideas is very excited to be offering the first public run of our Secure Coding for Web ...
Continue Reading
Scary Web Services: Part 1
I have several things I want to say about web services but for this post I am going to constrain ...
Continue Reading
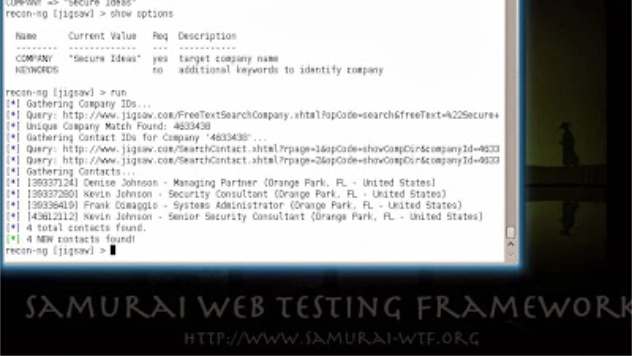
Professionally Evil Toolkit - Recon-ng
The first stage of almost every successful penetration test is the reconnaissance phase. During ...
Continue Reading
Who are we: Jason Gillam
In this series of posts we are introducing staff members at Secure Ideas to give you a quick ...
Continue Reading
Facebook Removes Privacy Settings (or Why it's hard to hide information on the Internet)
A few weeks ago Facebook announced the removal of a “Search” setting. That’s their marketing term ...
Continue Reading
Professionally Evil Perspective Podcast - Methodology Continues with Discovery
James and I recorded the next episode of the Professionally Evil Perspective podcast this morning. ...
Continue Reading
Web App Pre-Flight
I think that it is because of my background in software development that I am passionate about ...
Continue Reading
Has contents: true
Total pages: 40
Current page: 32