Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Burp Extension for F5 Cookie Detection
This past February, my fellow colleague James Jardine wrote an excellent blog post called “Decoding ...
Continue Reading
Defending Against Pass-the-Hash (PtH) Attacks
Pass-the-Hash (PtH) attacks have become probably the most common form of credential attacks used in ...
Continue Reading
Video: Introduction to Burp Suite
The below video is an introduction to Burp Suite. This is the first of our videos that will teach ...
Continue Reading
Kismet Log Viewer v2 Tool Released
Secure Ideas actively supports open source and giving back to the community. In that light, we’re ...
Continue Reading
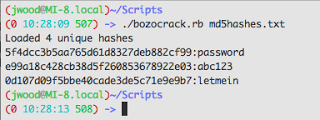
Professionally Evil Toolkit - BozoCrack
This week I’ve been teaching a class on web app security for developers and I remembered a fun ...
Continue Reading
Professionally Evil Perspective podcast: Mobile Security Testing - Tips and Tools
I have to say that I really enjoy doing the Professionally Evil Perspective (PEP) podcast with ...
Continue Reading
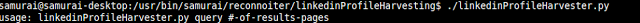
Professionally Evil Toolkit - Reconnoiter
In this series of the Professionally Evil Toolkit we will be talking about Reconnoiter. Reconnoiter ...
Continue Reading
Secure Ideas will not be presenting at DEF CON this year
James Jardine and I were accepted to present at DEF CON 21 in Las Vegas this year on attacking ...
Continue Reading
Who We Are: Thom Dosedel
Who am I: Thom Dosedel, Senior Security Consultant at Secure Ideas. What do I do at Secure Ideas: ...
Continue Reading
SamuraiWTF 5th Anniversary Giveaway
I am very excited to be writing this entry. As of August 10, 2013 the SamuraiWTF project will be ...
Continue Reading
Why Do Phishing As Part of Security Testing
I was recently watching a web cast on incident response and found myself thinking about the cause ...
Continue Reading
Has contents: true
Total pages: 40
Current page: 34