Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Beyond Hacking: Expanding Your Security Arsenal
Understanding the Need for Penetration Testing You’ve been told you need a penetration test. Maybe ...
Continue Reading
Quick Bites Episode 8 - (Back From the) Dead Space
hacking |
Quick Bites |
exploits |
MOVEit |
MOVEit Transfer |
SQL Injection |
Patching
For the last couple weeks, I’ve been replaying the original Dead Space trilogy - for those of you ...
Continue Reading
Understanding Server-Side Template Injection (SSTI)
Testing |
Training |
QA |
web penetration testing |
penetration testing |
application security |
OWASP |
web application security |
methodology |
OWASP Top 10
Web applications play a vital role in delivering dynamic content to users. To achieve this, ...
Continue Reading
Introducing SamuraiWTF 5.3: A Powerhouse for Web App Pen Testing
Testing |
Training |
samuraiWTF |
web penetration testing |
application security |
professionally evil |
Secure Ideas |
hacking |
OWASP |
Project
We are thrilled to announce the release of SamuraiWTF (Web Training Framework) version 5.3! This ...
Continue Reading
Introducing BILE - Groundbreaking Classification for Web App
Training |
penetration testing |
OWASP |
web application security |
BILE |
OWASP Top 10 |
BILE Classification Scheme |
vulnerability classification
As a seasoned web application penetration tester, I've always felt that there should be a more ...
Continue Reading
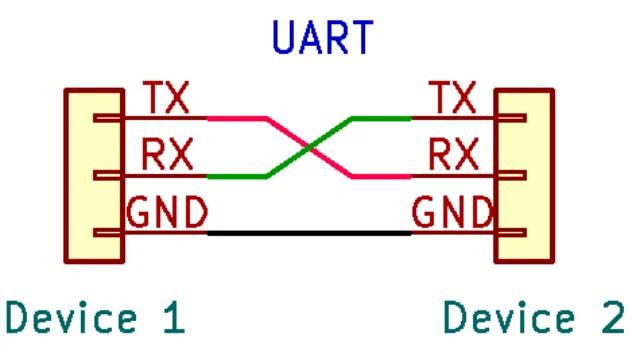
Hardware Hacking: Interfacing to UART with Your Computer
In my previous article, we covered identification and mapping of the UART interface. In that ...
Continue Reading
Hardware Hacking: Finding UART Pinouts on PCBs
In my previous article, we started to explore the Universal Asynchronous Receiver/Transmitter ...
Continue Reading
Hardware Hacking: Introduction to the UART Interface
I wanted to provide some information about hardware and firmware hacking in our blogs. To get the ...
Continue Reading
Introducing PETaaS®: Professionally Evil Testing as a Service
We're thrilled to announce the launch of our latest offering: Professionally Evil Testing as a ...
Continue Reading
Ace CISSP Exam Prep with ChatGPT: Your AI Study Buddy
Are you preparing for the CISSP exam or any other exam that requires a deep understanding of ...
Continue Reading
Has contents: true
Total pages: 40
Current page: 8