Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Quick Bites Episode 11 – Ranking Application Risks
application security |
hacking |
pentesting |
Quick Bites |
risk assessment |
appsec |
application risk |
ranking risk
Threats often evolve faster than defenders can figure out how to prevent them. That’s why keeping up with the threats and assessing the risk associated with them is so important. Here at Secure Ideas, we believe that assessing and ranking application risks is key. In this Quick Bites, we’ll talk ...
Continue Reading
Never miss a Professionally Evil update!
Quick Bites Episode 10 – Half Shells and Full Shells
hacking |
pentesting |
shell |
Quick Bites |
reverse shells |
terminal |
python |
python3 |
netcat |
command line |
nc
I wanted to share a really cool technique that I found out about recently. Now I will say this is ...
Continue Reading
Exploring Sentry Safe Exploit on the Flipper Zero with Logic Analyzer
hacking |
hardware |
flipper zero |
sentry |
safe |
logic analyzer
Overview I recently had a friend that wanted to learn how to use a logic analyzer. Given the number ...
Continue Reading
Flipper Zero: A Hardware Hacking Multitool Webcast
Training |
hacking |
hardware |
webcast |
flipper zero
The Flipper Zero is known as a hacking multitool. It can cover a range of hacking from sub-ghz ...
Continue Reading
CyberScream - Hacking Like a Ghost(face)
consulting |
data breach |
penetration testing |
professionally evil |
hacking |
analysis |
cybersecurity |
pentesting |
phishing |
security breach |
exploits |
Halloween |
webcast
It’s that most hauntingly wonderful time of year again! Halloween is upon us, along with the dread ...
Continue Reading
Quick Bites Episode 8 - (Back From the) Dead Space
hacking |
Quick Bites |
exploits |
MOVEit |
MOVEit Transfer |
SQL Injection |
Patching
For the last couple weeks, I’ve been replaying the original Dead Space trilogy - for those of you ...
Continue Reading
Introducing SamuraiWTF 5.3: A Powerhouse for Web App Pen Testing
Testing |
Training |
samuraiWTF |
web penetration testing |
application security |
professionally evil |
Secure Ideas |
hacking |
OWASP |
Project
We are thrilled to announce the release of SamuraiWTF (Web Training Framework) version 5.3! This ...
Continue Reading
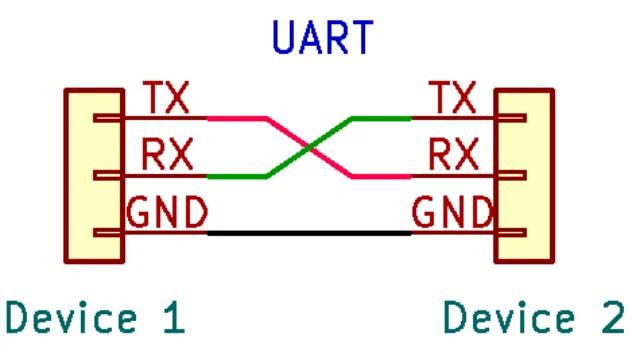
Hardware Hacking: Interfacing to UART with Your Computer
In my previous article, we covered identification and mapping of the UART interface. In that ...
Continue Reading
Hardware Hacking: Finding UART Pinouts on PCBs
In my previous article, we started to explore the Universal Asynchronous Receiver/Transmitter ...
Continue Reading
Hardware Hacking: Introduction to the UART Interface
I wanted to provide some information about hardware and firmware hacking in our blogs. To get the ...
Continue Reading
Quick Bites Ep 5 - The Call Is Coming From INSIDE THE HOUSE
hacking |
Quick Bites |
Insider Threat |
Attacks |
Halloween
Man, I’ll be honest - I’m super excited to be doing a Halloween-themed blog post this year. So, ...
Continue Reading
Nmap vs. Masscan
hacking |
NMAP |
port scanning |
masscan |
host discovery
If you are in IT, chances are you have at least heard of Nmap and Masscan. Both are free and ...
Continue Reading
Has contents: true
Total pages: 2
Current page: 1