Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
The Real AI Revolution in Penetration Testing
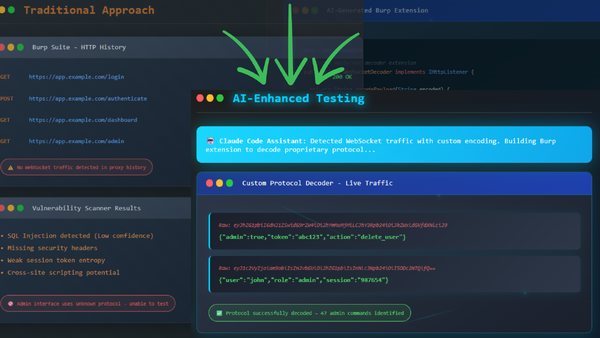
Custom Tooling at Lightning Speed Most cybersecurity professionals hear "AI in penetration testing" and immediately think of automated vulnerability scanners or AI-powered report generation. They're missing the real revolution happening right now in security testing, and it's not what you think. ...
Continue Reading
Never miss a Professionally Evil update!
Quick Bites 13 – Network Pentest Restrictions Can Hurt Your Business
Too Many Network Pentest Restrictions Can Hurt Your Business
Continue Reading
Risk-Driven Approach: The Federal Government’s Shift in Cybersecurity Burden
From All-Hazards to Risk-Informed The New Risk-Informed Paradigm One of the most significant shifts ...
Continue Reading
Understanding Garbage Findings
There is a well-meaning desire among penetration testers to produce findings. The fact of the ...
Continue Reading
Houston, We Have a Problem
Satellite Security Testing: A Holistic Approach Last month, I had the opportunity to present at ...
Continue Reading
When Algorithms Aren’t Enough: Why the Human Element Still Matters in Modern Penetration Testing
The cybersecurity industry has evolved into two distinct approaches when it comes to penetration ...
Continue Reading
Solicited Public Comment on HIPAA Security Rule NPRM To Strengthen the Cybersecurity of ePHI
The Department of Health and Human Services (HHS) wants to raise the benchmarks of the Security ...
Continue Reading
The CISO's Myopia
Fifteen years ago, I wrote an article entitled "The CSO’s Myopia." At the time, I aimed to ...
Continue Reading
Mobile Testing Considerations
penetration testing |
Secure Ideas |
cyber security |
mobile application security testing |
mobile app penetration testing |
mobile application development |
mobile application testing |
testing mobile applications |
iOS certificate pinning |
mobile application vulnerability assessment |
mobile application security assessment |
mobile app security analysis |
secure mobile application development practices |
android app security testing |
iOS app security testing |
android certificate pinning |
MobSF
Testing In Mobile Applications In today’s world, the significance of mobile applications in our ...
Continue Reading
The reason I stopped using Postman for API Pentests
I’ve been a proponent of Postman for a number of years. I’ve written and spoken about using it in ...
Continue Reading
CyberScream - Hacking Like a Ghost(face)
consulting |
data breach |
penetration testing |
professionally evil |
hacking |
analysis |
cybersecurity |
pentesting |
phishing |
security breach |
exploits |
Halloween |
webcast
It’s that most hauntingly wonderful time of year again! Halloween is upon us, along with the dread ...
Continue Reading
Navigating Evolving Regulations: Staying Ahead of Change
In today's rapidly expanding business world, the only constant seems to be change itself. One of ...
Continue Reading
Has contents: true
Total pages: 2
Current page: 1
.jpg)