Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
CyberScream - Hacking Like a Ghost(face)
consulting |
data breach |
penetration testing |
professionally evil |
hacking |
analysis |
cybersecurity |
pentesting |
phishing |
security breach |
exploits |
Halloween |
webcast
It’s that most hauntingly wonderful time of year again! Halloween is upon us, along with the dread of Q4. Are compliance horrors putting you in a ‘SAW’ like predicament, compelling you to navigate through agonizing trials just to make it to the end of the year alive? Secure Ideas’ resident Horror ...
Continue Reading
Never miss a Professionally Evil update!
Introducing SamuraiWTF 5.3: A Powerhouse for Web App Pen Testing
Testing |
Training |
samuraiWTF |
web penetration testing |
application security |
professionally evil |
Secure Ideas |
hacking |
OWASP |
Project
We are thrilled to announce the release of SamuraiWTF (Web Training Framework) version 5.3! This ...
Continue Reading
How to iterate through advfirewall rules
Training |
professionally evil |
Secure Ideas |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
powershell |
firewall rules
There are several ways to pull firewall information from a Windows system. Today we will leverage ...
Continue Reading
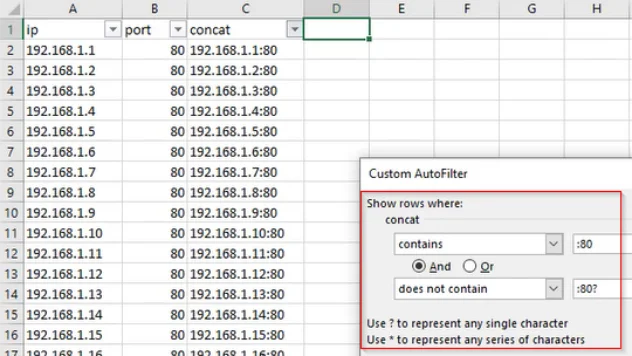
Working With Data: IP and Port Filtering
Training |
professionally evil |
Secure Ideas |
technology tips and tricks |
sysadmin |
data |
data manipulation |
excel |
spreadsheet |
filtering
During our day-to-day work, there’s a lot of data that we interact with. In order to make good use ...
Continue Reading
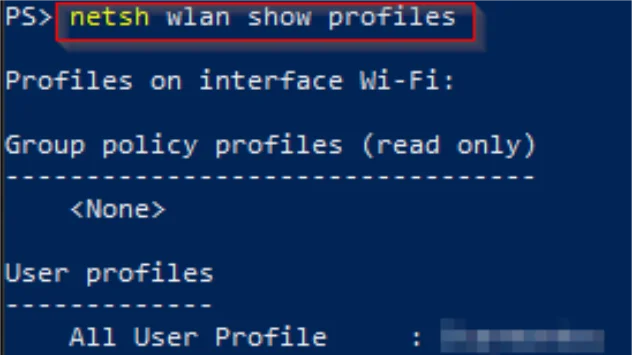
View Wireless Profile Password Information Using PowerShell or CMD
Training |
professionally evil |
Secure Ideas |
hacking |
Windows |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
wireless |
wifi |
wifi password |
powershell |
wireless profile
There are a couple different ways for you to access your Windows wireless password information. If ...
Continue Reading
Application Security 202: Vulnerabilities Accepted
Testing |
Vulnerability |
Guidance |
data breach |
information security |
penetration testing |
application security |
professionally evil |
Secure Ideas |
hacking |
best practices |
cybersecurity |
Privilege Escalation
vul·ner·a·bil·i·ty The quality or state of being exposed to the possibility of being attacked or ...
Continue Reading
Privilege Escalation via File Descriptors in Privileged Binaries
application security |
professionally evil |
Secure Ideas |
Linux |
programming |
File Descriptors |
SetUID |
Privilege Escalation
Today I wanted to cover an application security topic that applies to SetUID binaries. As we all ...
Continue Reading
How to Update the Nmap OUI Database
network |
professionally evil |
Secure Ideas |
NMAP |
Linux |
IEEE |
OUI |
nmap-mac-prefixes
Overview In a previous blog post, I covered what an OUI is, how to extract them from a MAC address, ...
Continue Reading
Of MAC Addresses and OUI: A Subtle, but Useful, Recon Resource
network |
professionally evil |
Secure Ideas |
MAC Address |
IEEE |
OUI |
PENT
When it comes to reconnaissance, every little bit of information can be helpful. Today, we will ...
Continue Reading
LD_PRELOAD: Making a Backdoor by Hijacking accept()
application security |
professionally evil |
Secure Ideas |
LD_PRELOAD |
accept |
dup2 |
make |
Linux |
programming |
Shared Objects |
dlsym |
shell |
backdoor |
rootkit |
userland |
ELF |
inject |
injection
Today I want to continue the series on using LD_PRELOAD. In previous posts, we covered how to ...
Continue Reading
PowerShell Tips: How do I Mount a VHD or Lock a BitLocker Drive?
encryption |
security |
professionally evil |
Secure Ideas |
getting started |
BitLocker |
VHD |
rtfm |
manage-bde |
mount-vhd |
manage bitlocker |
technology |
technology tips and tricks |
Windows 10 |
VHDX |
encrypted drive |
technology tips |
how-to |
btfm |
Windows 11
PowerShell Tips How do I Mount a VHD or Lock a BitLocker Encrypted Drive?
Continue Reading
Has contents: true
Total pages: 1
Current page: 1