Knowledge Center
Get the answers you need to choose the right security services for your organization..
But AI Can Give Me the Commands! Why You Still Need to Learn the Linux File System
Linux |
AI |
AI Security
It’s now easier than ever for AI to write your bash scripts or give you the exact command to ...
Continue Reading
How to Get the Most Out of Your Penetration Test: A Guide to Preparation and Success
When it comes to penetration testing, preparation isn't just helpful—it's essential for success. ...
Continue Reading
Countdown to Full Compliance: PCI-DSS 4.0.1
As the deadline for full compliance with PCI DSS v4.0.1 approaches, organizations should be turning ...
Continue Reading
Red Team vs. Purple Team: What's the difference?
Red Team vs Purple Team In today's world, security threats are at an all-time high, and ...
Continue Reading
What is CMMC 2.0 and How Does it Impact Your Organization?
Someone once asked bank robber Willie Sutton why he robbed banks. Sutton replied, “Because that's ...
Continue Reading
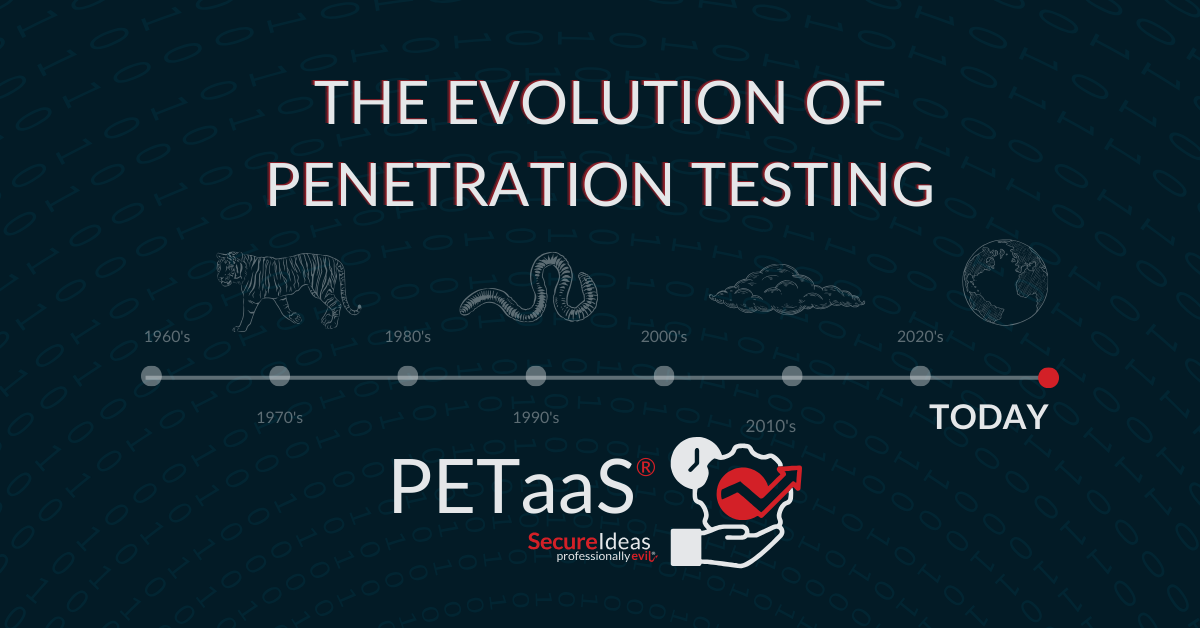
The Evolution of Penetration Testing
How a Proactive Approach Promotes Organizational Cyber Resilience Just a decade ago, the importance ...
Continue Reading
Straight Facts: Testing as a Service Dispatches the Goods
Most InfoSec professionals recognize that technological advancements are rapidly changing how we ...
Continue Reading
How much does a Penetration Test Cost?
How much does a penetration test cost? If you are reading this then you or your organization has ...
Continue Reading
What is a Threat-Led Penetration Test?
Testing |
penetration testing |
hacking |
cybersecurity |
business |
directive |
Responsibilities |
experts |
compliance |
banking |
government |
standards |
cybersecurity standards |
framework |
DORA |
EU
Penetration testing comes in many forms, encompassing everything from network and application ...
Continue Reading
Unleashing the Power of Hackathons
What is a Hackathon? A security hackathon is a structured event where we collaborate with clients ...
Continue Reading
Buckle Up: Ride Along with the Professionally Evil Experts
A ride along penetration test is a collaborative cybersecurity assessment where our penetration ...
Continue Reading
Navigating the California Consumer Privacy Act (CCPA)
What is the CCPA? Regulations like the California Consumer Privacy Act (CCPA) are driving how ...
Continue Reading
Has contents: true
Total pages: 7
Current page: 0