Strengthen Your Security with Penetration Testing
Penetration testing – also known as ethical hacking or pentesting – is a proactive cybersecurity endeavor where security experts simulate real-world cyberattacks to uncover vulnerabilities in computer systems, networks, web applications, and underlying infrastructure. The objective is to detect potential weaknesses that can be remediated before threat actors can exploit them.
The penetration testing process identifies vulnerabilities and evaluates an organization’s capacity to detect, respond to, and mitigate cyber threats effectively. Organizations gain an authentic understanding of their cybersecurity posture, enabling them to assess the effectiveness of existing security measures.
Put simply: When you know what's happening, you know where to put your energy.
Penetration testing gives decision makers the knowledge to implement targeted security enhancements and improve their incident response plans. The information gathered enables business leaders to make wise investments in cybersecurity.
Jump to Section
- Network penetration testing: The aim of network testing is to identify vulnerabilities that an attacker could exploit to gain unauthorized access to the network, alongside data and corporate assets. Pentesters focus on the network’s infrastructure and may also examine network devices such as firewalls, routers, and switches to ensure controls in place are operating effectively.
- Application penetration testing: Application-based penetration tests focus on the security posture of web and desktop applications. Experts interact with these applications to find ways to tamper with configuration settings, steal data, or circumvent authentication measures. Third-party integrations and code may also be examined.
- Mobile penetration testing: Mobile penetration testing services focus on apps, including those developed for the Google Android and Apple iOS ecosystems.
- API penetration testing: Application Programming Interface (API) pentesting examines API endpoints and infrastructure, mapping API structures and identifying weaknesses.
- Red Team engagements: Red team engagements simulate real-world attacks to test an organization’s preparedness and response.
- Purple Teams engagements: Purple team engagements combine a red team and blue team, the existing members of an organization’s security center. These groups collaborate to improve existing defense mechanisms.
- Physical penetration testing: Security experts test the security of physical controls with the goal of identifying vulnerabilities and weaknesses in employee awareness and procedures to obtain unauthorized access, including offices, areas of business, and data centers. Doors, windows, and locks may all be in scope.
- IoT and embedded device testing: Specialist knowledge is required to fully test Internet of Things (IoT) and embedded devices. Each endpoint could be exploitable, so it is important that penetration tests include firmware, network interfaces, access controls, interactions with third parties, and even wireless communication protocols.
Why should your organization perform penetration tests?
Today’s businesses conduct penetration tests to meet numerous goals. First and foremost, penetration tests are performed to uncover underlying security problems in software, network architecture, access controls, and devices. They may also be conducted to test an existing team’s response to cyberattack scenarios.
Today, penetration tests may be required by law to meet compliance requirements – such as those laid out by PCI DSS – and they can also benefit an organization by providing security assessments for use in the creation of risk management strategies. Furthermore, penetration tests highlight a dedication to security to potential clients, increasing customer trust.
Thousands of new vulnerabilities are discovered every year. It can be impossible for organizations to keep track of each flaw or to recognize which ones present the greatest risk to an organization.
Endless patch loops are not the answer. Instead, managing defense requires risk-based assessments and frequent penetration testing.
The cyberthreats most likely to harm organizations today include network intrusion, zero-day vulnerabilities, and ransomware. Software weaknesses include cross-site scripting (XSS) flaws, improper authentication bugs, access control errors, and security misconfigurations.
There are resources available that provide a thorough groundwork on the most significant risks to businesses today. As a baseline, we recommend Mitre’s CWE Top 25 Most Dangerous Software Weaknesses and OWASP Top Ten security awareness documents as starting points as organizations work to strengthen their security programs.
Read more:
- What Risks Does the Dark Web Pose to Businesses?
- Four Steps to Prepare your Application for a Denial of Service Attack
- Top Ten AWS Security Configurations: Mitigating Risk in the Cloud
- The Client-Side Security Trap: A Warning For Developers
- What are SQL Injection Vulnerability (SQLi), How to Identify Them, and How to Prevent Them
You can only protect yourself against the weaknesses you know about. Penetration testing helps you find those weaknesses.
A penetration test is a proactive way to ensure an organization is taking the necessary action to adequately secure their systems and data against malicious intrusions. Regularly conducting penetration tests identifies hitherto-undiscovered weaknesses which might otherwise lead to data breaches or other equally serious security incidents.
Read more:
Penetration testing systematically pinpoints your network’s and website’s vulnerabilities. You can use this information to measure the effectiveness of your existing security controls, patch security flaws, improve incident response, and meet the compliance standards required by regulations, including but not limited to HIPAA, PCI DSS, and GLBA.
The findings of your penetration test are provided in a detailed report. The report has an executive overview describing the engagement’s purpose and a summary of the results, presented in a clear, non-technical format. That’s followed by a detailed narrative that walks you through the penetration testing team’s thought process, procedures, and discoveries. This narrative provides crucial context for the findings, especially in complex scenarios or when few vulnerabilities are discovered. Each finding is summarized, described in specific technical detail, and linked to an actionable and practical recommended remediation path.
Consider these factors in your decision:
- Expertise and Specialization: Penetration testing requires specific skills and up-to-date knowledge of evolving threats and techniques. Evaluate whether your in-house team can maintain this specialized expertise or if external specialists might be beneficial.
- Resource Allocation: Consider your organization's size, budget, and frequency of testing needs. Determine if you have enough ongoing work to justify a full-time in-house penetration tester or if outsourcing provides more flexibility.
- Compliance Requirements: Some regulatory frameworks may require specific certifications (e.g. CREST). Review your compliance needs to ensure your chosen approach satisfies these requirements.
- Contractual Obligations: Some client or partner contracts may stipulate independent third-party security assessments or require a letter of attestation. Ensure your penetration testing strategy aligns with these obligations.
- Objectivity and Fresh Perspective: External testers can offer an unbiased and objective view of your systems, potentially uncovering blind spots that in-house teams might overlook.
- Knowledge Transfer: Whether in-house or outsourced, consider how penetration testing insights will be shared and integrated into your overall security strategy.
- Hybrid Approach: Many organizations find value in combining in-house security expertise with periodic external assessments, leveraging the strengths of both approaches.
Ultimately, the choice between in-house and outsourced penetration testing depends on your organization's specific needs, resources, and long-term security strategy. Carefully weigh these factors to determine the most effective approach for your situation.
- Security programs: Existing in-house security specialists have a lot to keep up with. Can they stay up-to-date with security testing processes? Generalists are great… until they aren’t. It may be wise to capitalize on the dedicated expertise of independent pentesting firms.
- Budgetary considerations: What can you afford? Does the organization have enough ongoing work to keep an expensive specialist busy? If not, an idle pentester is an expensive proposition.
- Compliance: Regulatory compliance may be a factor. You may need to hire companies with specific certifications and qualifications, or you may be unable to meet legal demands from your existing in-house teams.
- Contractual obligations: Contractual obligations that require third-party attestation of your system’s security may necessitate the assistance of an outsourced penetration testing service.
- Roles: Conducting a penetration test requires specific skills and experience. It can be difficult to hire enough professionals for in-house roles to manage consistent penetration testing, so outsourcing may be more realistic and cost-effective.
Ideally, organizations would acquire cybersecurity expertise through a skilled in-house team and a trusted partner (such as Secure Ideas). However, realistically, this may be a difficult prospect considering time, budgetary constraints, and the ongoing cybersecurity staff shortage.
Read on:
The cost of penetration test services varies considerably based on the client's specific needs and requirements.
The most significant factors are the scope of an engagement and the effort required. For example, the time and effort required to test a small web application is significantly less than a penetration test of an entire corporate network and its associated assets.
The time and effort demanded by a penetration test depends on its scope. Typically, a penetration test costs between $10,000 and $45,000. That’s a wide range, but the estimate varies depending on whether you need a standalone test or continuous testing, whether you purchase credits for on-demand pentests and analysis, or whether your project has special reporting requirements. Volume discounts may also be available when multiple tests are quoted.
Secure Ideas’ penetration testing services are ethical and prioritize the safety and security of your intellectual property and assets. Our cybersecurity experts thoroughly examine every in-scope system to identify exploitable flaws and security weaknesses while avoiding unnecessary risks to your business operations.
Responsibility is at the core of our services. We pledge to handle your assets and information with discretion and ethical care.
Read more:
What factors should I consider in setting up a penetration test?
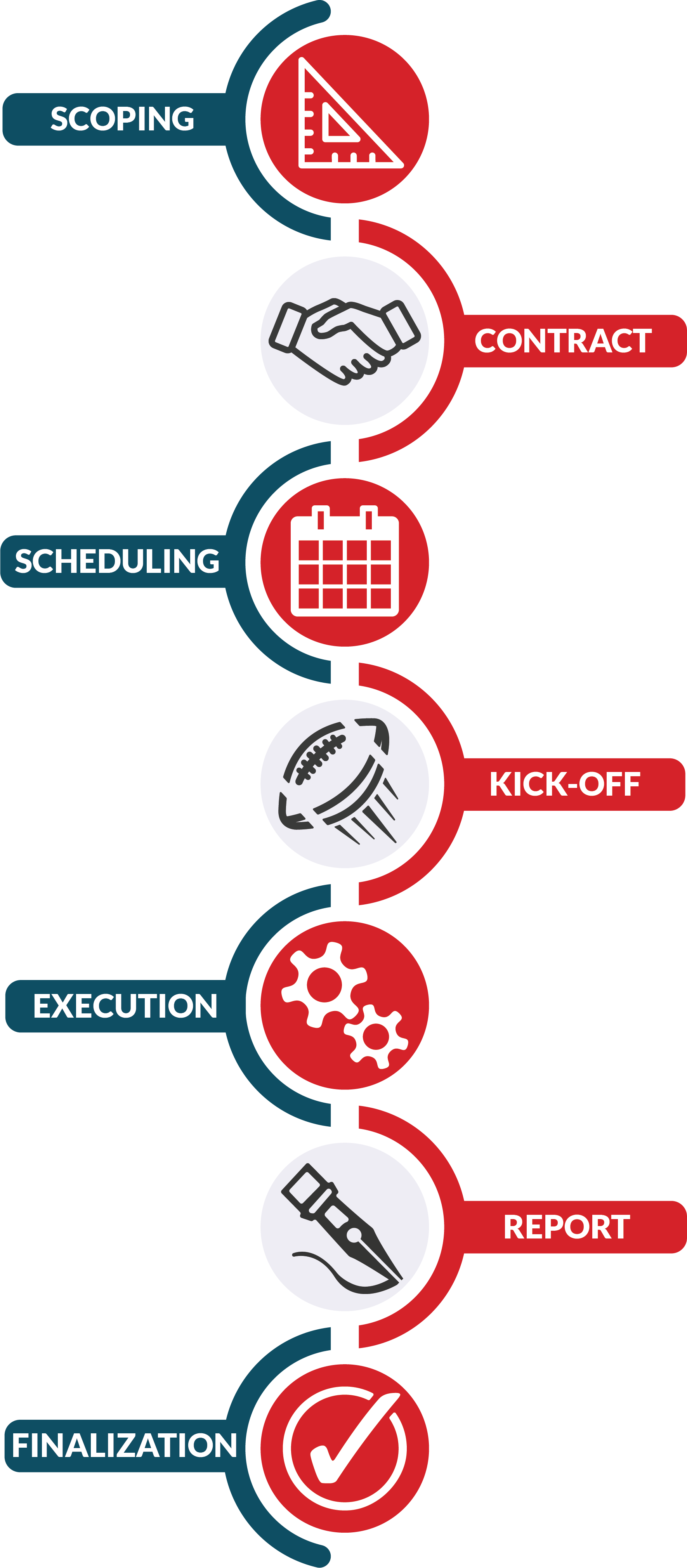
Once you decide to conduct a penetration test, you need to determine the engagement’s scope.
Map the plan to meet your goals. A single test might be sufficient to meet compliance requirements, such as a checkbox for a contract your organization wants. However, if you aim to improve your organization’s overall security posture, regular penetration tests can be more effective. Make those needs and goals concise and clear before you engage a third party. This ensures that your chosen partner can meet expectations. During this preliminary process, consider:
- Timelines: Do you have a timeline that needs to be met? Or is scheduling flexible?
- Scope: Determine which systems, networks, and applications should be tested, noting sensitive assets that might need to be removed from scope or tested with extreme caution so as not to disrupt operations.
- Black, gray, and white box testing: Do you need to provide information and code for target systems?
- Specific requirements: Do you need specific tests or reviews? Is a full penetration test required, or do you need to focus on specific areas?
- Budget: How much have you allocated to cybersecurity initiatives? What budget allocation is suitable, or available, for a penetration test? If the budget doesn’t stretch to cover everything on your requirements list, what changes are you able to make to the budget or the scope?
- Regulations: Is a penetration test necessary to meet compliance requirements with specific regulations? If so, which regulations, and how frequently must testing be conducted?
Once this information has been provided, expect a formal statement of work (SoW) that outlines the description of services, the engagement's goals, methodologies, in-scope assets, and objectives.
Organizations usually plan penetration tests well in advance. However, if flexibility is required, note that Secure Ideas’ test credits permite organizations to prepare for upcoming tests without specifying an exact scope.
Read more:
- A Step-by-Step Guide to Penetration Testing For Beginners
- What is the Scope of a Penetration Test?
- 8 Challenges That Can Hinder Effective Penetration Testing
- How To Prepare for a Penetration Test
What Should be Tested?
Penetration testing experts can help you tailor elements that match your organization's unique requirements. Those are based on risk assessments and regulatory or compliance requirements.
For instance, you might have attention on specific areas of the corporate environment, such as a network, data center, or legacy computing assets. A recent security incident would make you sensitive to additional vulnerabilities to explore.
Pay attention to compliance requirements. If your organization handles sensitive information, it may need to meet specific standards such as PCI DSS, which would require the Cardholder Data Environment (CDE) to be included in the project scope.
Don’t try to get too granular. When in-scope tests are too narrow, vulnerabilities and security flaws can be overlooked, which may impact the overall quality of a penetration test and the usefulness of its recommendations.
Protecting any non-public, sensitive datasets should be the top priority. This includes confidential and proprietary information that belongs to an organization or its customers, such as Protected Health Information (PHI), financial and banking information, and potentially non-public personally identifiable information (PII), depending on the context and content of the records. That includes proprietary data, including intellectual property, employee records, contracts, and legal documents.
Scheduling
The frequency of penetration tests is determined by a client's unique needs and security challenges.
Many of today’s security standards, including NIST 800-53 and ISO/IEC 27001, recommend penetration testing but do not specify exact timelines. Data protection laws, such as PCI DSS and HIPAA, also promote regular security evaluations.
PCI DSS, for example, requires at least an annual penetration test or one after any significant environmental changes. Additionally, frequent segmentation validation of the Cardholder Data Environment (CDE) against non-CDE environments may be necessary. The maturity of your existing security program, specific regulatory and compliance demands, and customer and service level agreements determine the best schedule for you.
Read more:
How should my team prepare for a penetration test?
Assemble the appropriate information before a pentest engagement begins. That may include technical information and asset lists depending on the project scope. Your penetration testing partner will conduct a kick-off meeting before the test’s official start date. This is typically held a few weeks prior to the start of an engagement to allow sufficient time to prepare. Together, you’ll set expectations: review the scope, contact information, schedule, rules of engagement, and any action on indications of compromise (IoC). In addition, the team should discuss whether any sensitive systems are in scope.
Read more:
Trustworthy penetration test providers follow a methodology as defined by the Penetration Test Execution Standard (PTES). During the execution phase, the teams perform activities that may include threat modeling, reconnaissance, vulnerability discovery, exploitation, and potentially post-exploitation.
Under ordinary circumstances, the active testing window for most penetration tests varies from three to ten days, depending on the test scope.
The total time of an engagement, including pre-engagement activities and reporting, typically ranges from two to four weeks; the practical test and report often takes an additional one to two weeks.
However, the timeline for a penetration test depends on scope, budgetary considerations, requests for specialized requests or deliverables, and time frame constraints. (That’s a long winded way of saying, “It depends.”)
We provide a detailed report for both technical and non-technical audiences, combined with practical, realistic, and actionable remediation guidance. The time required to issue reports and deliverables depends on the scope of your penetration test and the testing window available. For instance, a limited, short pentest with a five-day testing window takes less time to analyze and compile a report than does an extensive, full network and physical asset penetration test.
We design and refine our deliverables to make a clear, transparent, and concise case for the necessary changes. We also ensure that both technical and executive personnel can process and understand our findings in a digestible, clear manner.
We aim to help teams prioritize the areas of greatest concern and risk while assisting key stakeholders in making informed, rapid decisions that benefit their business. Our intent is that these reports help organizations get better support from upper management to strengthen their security posture. Secure Ideas, as a trusted third-party and subject matter expert, can provide recommendations to key stakeholders that might not get the recognition deserved when previously raised by the organization’s personnel.
Typically, clients are given five business days to review and respond once a report is issued. For example, clients may wish to update or request changes to the final report, such as changing risk indicators based on business processes or after the provision of further information.
Once a report is accepted and finalized, Secure Ideas may conduct formal presentations and executive-level overviews or discuss the report’s findings in depth with technical staff. The issuance of a report and suggestions for remediation doesn’t necessarily mean the end of the journey. Penetration testers may provide further consultancy and advisory services, offering additional strategic guidance on tackling emergent security issues.
The time required for remediation and resolving any concerns raised by a penetration test is determined on a case-by-case basis. It may depend on an organization’s security program maturity level, resources, and the number and nature of issues needing to be resolved.
At Secure Ideas, we typically request that any retesting is scheduled and completed within 90 days of a final draft report being delivered, but this time frame can be flexible depending on the client’s needs.
Schedule developer agile cycles to remediate security issues
Traditional, standalone penetration tests are not always compatible with the agile nature of today’s software development lifecycle (SDLC) and DevOps workflows.
Instead, we recommend a series of steps to embed security testing within the SDLC processes. While we go into detail in a blog post on the subject, the problem should be tackled in three steps:
- Training: Security training should benefit development teams, not disrupt their projects or overwhelm them. You can opt for internally or externally maintained training, or both, to keep training digestible and suitable for compliance purposes.
- Advisory: Create an advisory program built on the foundation of effective training. Advisors should have development experience to understand goals, procedures, and concerns.
- Assistance: Your training program must include assistance, such as live guidance, testing platforms, and frequent reviews.
What is an Attestation Letter?
An attestation letter, also known as an Executive Summary Report, is a statement or declaration from an independent third party. These letters lend credibility to the organization under review by confirming specific actions or behaviors.
Attestation letters, such as those provided by Secure Ideas, are essential components of the audit process. After a penetration test is completed, attestation letters can confirm that the organization has adequate protection in accordance with industry standards and regulations. They introduce an independent layer of trust.
Read more:
Frequently Asked Questions: Learn more about Penetration Testing
Why do I need a penetration test?
A penetration test shows an organization is being proactive and taking the necessary steps to ensure the resilience of digital assets and data against malicious intrusions. Through penetration testing, vulnerabilities within your infrastructure are systematically pinpointed and then rectified, enhancing overall defenses.
This proactive approach aids organizations in averting potential data breaches and security incidents. Moreover, companies that demonstrate a commitment to security gain a competitive edge, increase brand trust, and experience a less fraught journey to achieving compliance with many of today’s stringent data protection laws.
What's the difference between penetration testing and vulnerability scanning?
Penetration testing actively simulates cyberattacks to exploit vulnerabilities and assess an organization’s security posture. Security professionals conduct controlled attempts to breach a system, mimicking real-world attackers' behavior.
In contrast, vulnerability scanning is a passive process that uses automated tools to identify and catalog potential weaknesses within a system or network. It generates a list of vulnerabilities by comparing the system's configuration and software against databases of known security issues and bugs.
While penetration testing is conducted periodically for a thorough analysis, vulnerability scanning, as a baseline, should be performed regularly. Although vulnerability scanning can identify emerging vulnerabilities in a timely manner, relying upon these tools alone isn’t enough, as they lack the contextual factors required for a true assessment of network, application, and system security.
How long does it take to do a penetration test?
With some exceptions, the active testing window for most penetration tests varies from three to ten days, depending on the scope of the test. The total time of an engagement, including pre-engagement activities and reporting, will typically range from two to four weeks.
How often does my organization need a penetration test?
In most cases, a penetration test is necessary annually or whenever a significant change to the system or application occurs. Specific requirements may vary according to certain regulations, internal policies, and the scope of an engagement.