Welcome to the fourth blog introducing and exploring the features of Burp Suite.
Please visit Secure Ideas’ previous blogs on using Burp Suite at the following links:
As discussed previously, Burp is a tool used during web application testing that allows you to proxy traffic to see what each aspect of the web application is doing. The first step in testing web applications is to ensure the client gives you explicit details to identify what is in scope during the test. The next step is to map the application. When mapping, you want to click on each tab and feature of the application. To demonstrate this step, we will be using SamuraiWTF, which can be found at the following link:
Samurai Web Testing Framework includes everything needed to get started in web application testing. Once you have downloaded the Samurai WTF VM, launch the VM in your favorite Virtual Machine application.
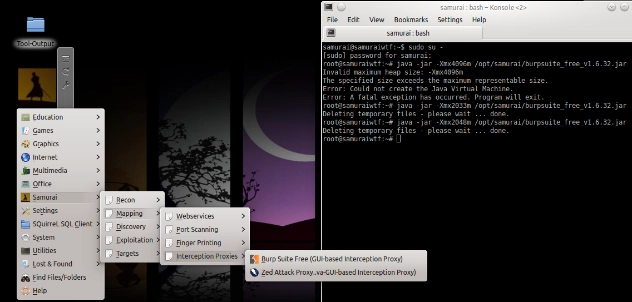
As before, we will launch Burp by starting via command line using terminal
#java -jar -Xmx2048m /opt/samurai/burpsuite_free_v1.6.32.jar
or simply select it from the desktop as shown below:
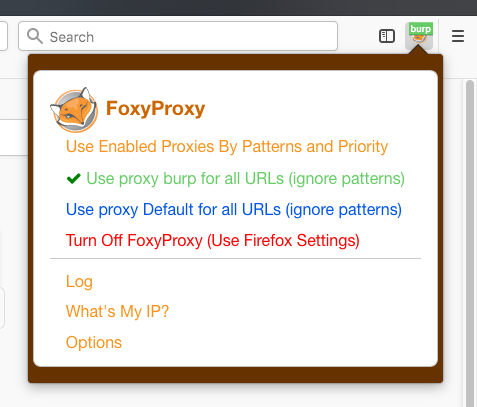
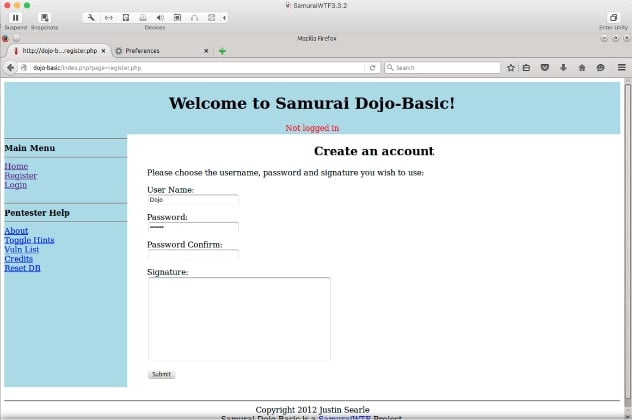
Samurai has a number of vulnerable web apps preinstalled to keep you from getting a visit from the men in black suits. For this post, we will be using dojo-basic. Simply open up the Firefox browser, click on the FoxyProxy icon next to the address bar and select Use proxy burp for all URLs.
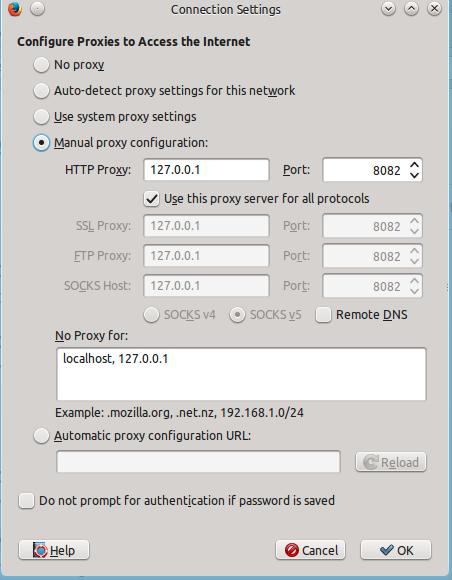
This will send all the web traffic through Burp so that you can view what each transaction is doing. If you do not see the FoxyProxy icon, go to browser settings and select preferences, then advanced, select network connection settings and enter in the information as shown below:
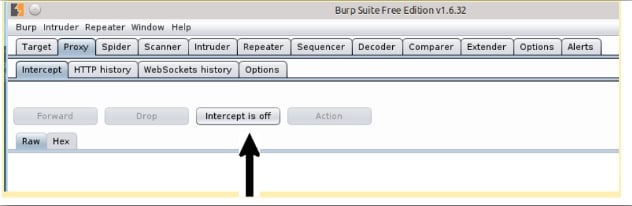
You will now see the web traffic being proxied through Burp and begin mapping out your web application. Burp also can intercept traffic, but for this blog we will need to ensure this feature is disabled. You can ensure intercept is disabled by selecting the proxy tab in Burp, then intercept and finally intercept is off as shown below:
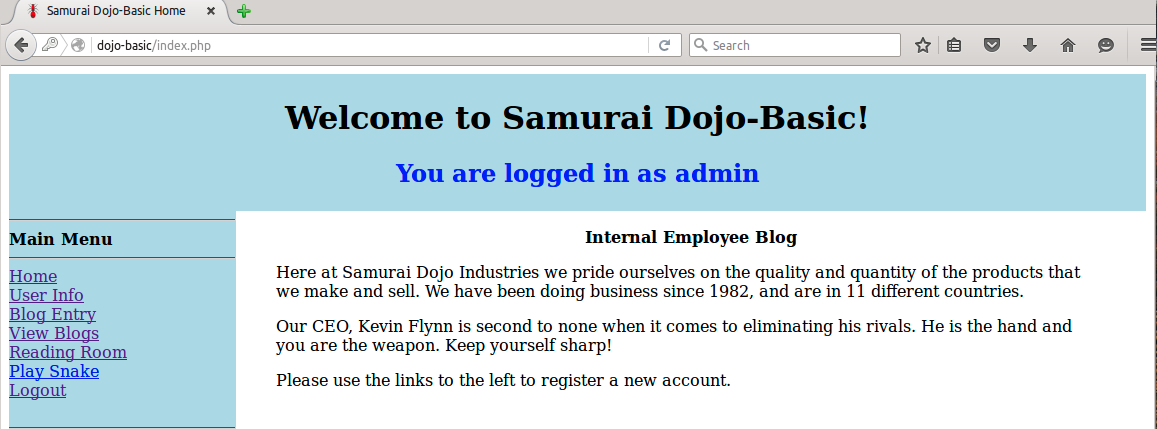
Ok, now all that is done, let’s get down to business! In your browser, type “dojo-basic” and press enter. You should now see the web page displayed. As you map the application by clicking on each link, the corresponding information will be seen in Burp. Go ahead and register for a user account and log in using the credentials you created.
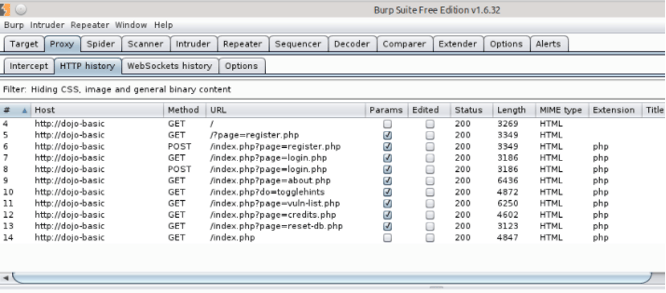
As you were mapping, Burp picked up each transaction that was performed in the application.
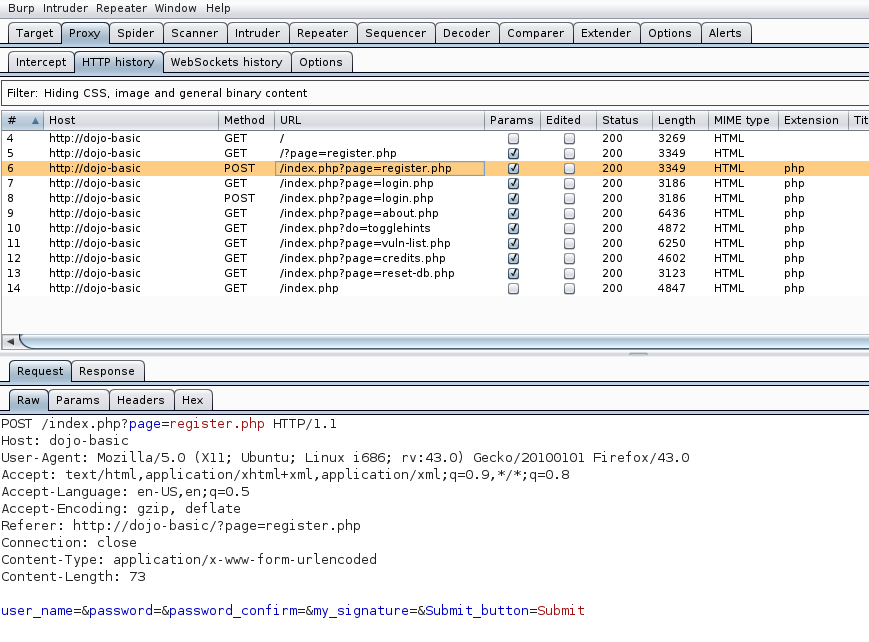
So let’s take a look at what we have. The first thing we want to look at is /index.php?page=register.php. Notice this is a POST transaction; this is a location where the user would be submitting information to register for an account to gain access to the application.
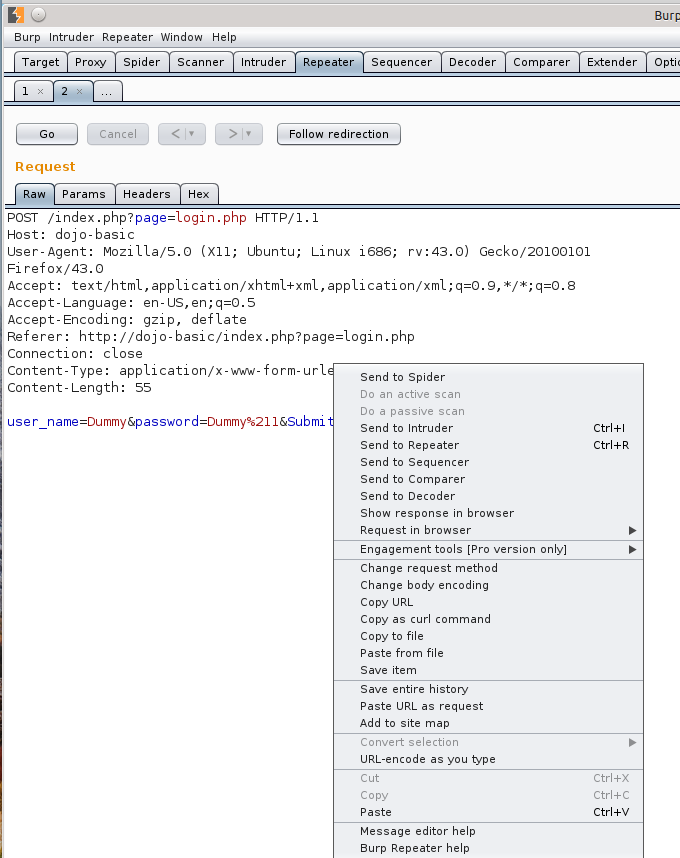
Right click on this transaction and add to scope the click Send to Repeater. You will see the Repeater tab at the top will now turn to orange. Select the Repeater tab and click Go. This will give you a display of the action before anything has been changed to the application in case you want to restart fresh. Before we go any further, let’s take a minute to see what is actually happening in the application. A lot of times the developer will leave default information and perhaps certain items that may be interesting to a would-be attacker such as default folders or outdated versions of software.
So if you don’t see anything interesting, let’s proceed. Our goal is to manipulate things like cookies and aspects of the site that may affect the rendering of the site. Often by manipulating the cookies we can find things like Authorization Bypass and gain access to an elevated user account. Play around with the cookies and the user_name and see if you can get a change in responses. We will not be going into a lot about repeater because we have touched this previously in a separate Secure Ideas blog.
Next, let us look at the Intruder tab, a lot of logins can be cracked with custom search list or using an available file that is easily obtainable. Often users are pretty set in their ways and hate using multiple passwords for the many websites and accounts they use daily.
We have found that a large majority of users still use the old password schema of the season and the year. It is surprising that simply trying Winter2018! will open up an account. Remember that it only takes one compromised user to gain access to your entire site or even network. Enough of me ranting, let’s keep moving along, there is nothing more to see here.
While we are still logged in to our Dojo-Basic site and in Repeater right click in Repeater and select Send to Intruder.
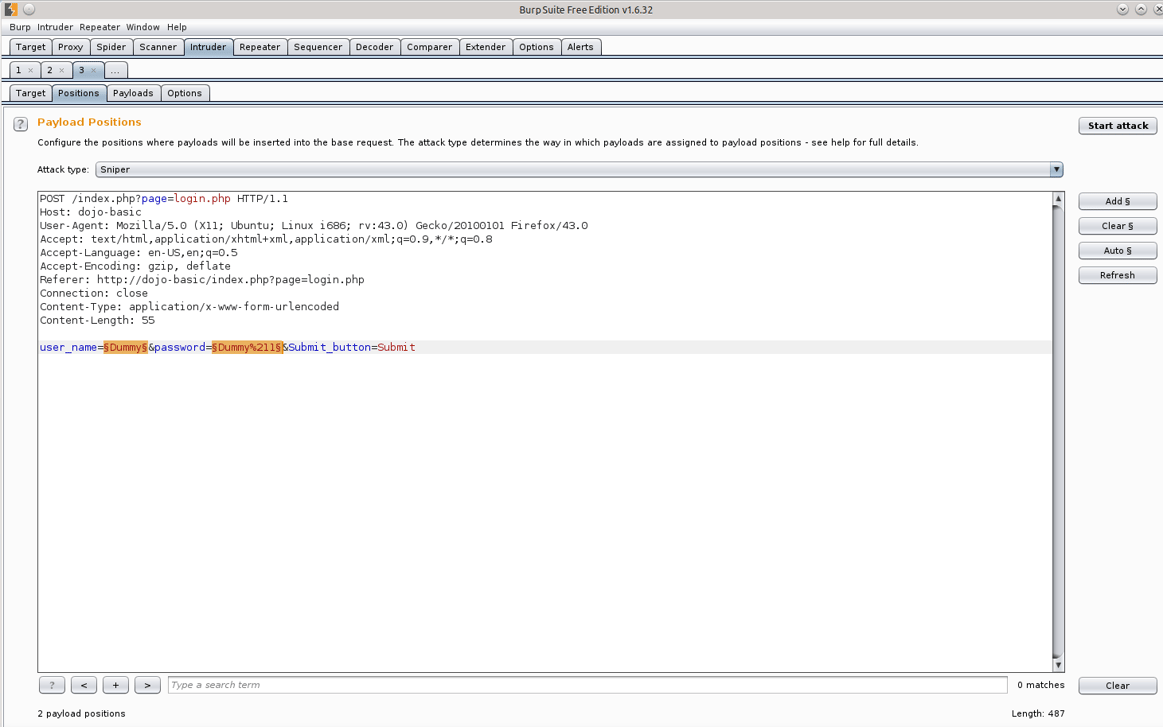
Your first step in Intruder is to set up the positions we want to target. Clear any currently highlighted positions and add a new position by highlighting information after user_name= and password= as shown in the next screen capture.
You will also need to decide if you want to target a single position or multiple positions. You can select the Sniper Attack or Battering Ram for single, and Cluster Bomb or Pitch Fork for multiple positions. We will be using Cluster Bomb in this scenario. Cluster Bomb will actually try every combination of usernames and passwords in the list.
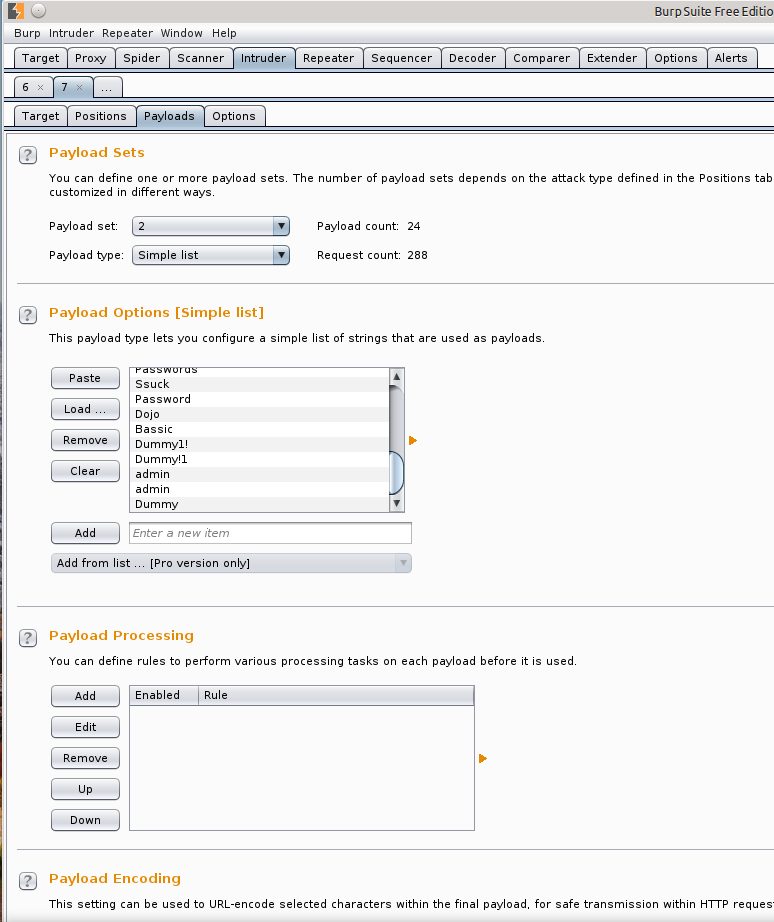
Now set the payloads by selecting the Payloads tab. We will be using a payload set of 2 and a payload type as simple list and utilize a text list we have already prepared. A usable word list can also be found in the /opt/samurai/fuzzdb/wordlists-user-passwd directory or you can create your own.
After the payloads are set and the payload options are loaded hit start attack. This step will take some time to complete, so now would be a great time to play fetch with the dog or grab a nice cold beverage from the fridge. Be aware this action will cause a lot of noise and can cause account lockouts. Using the list you provide Intruder will try every possible pattern until the entire list has been used.
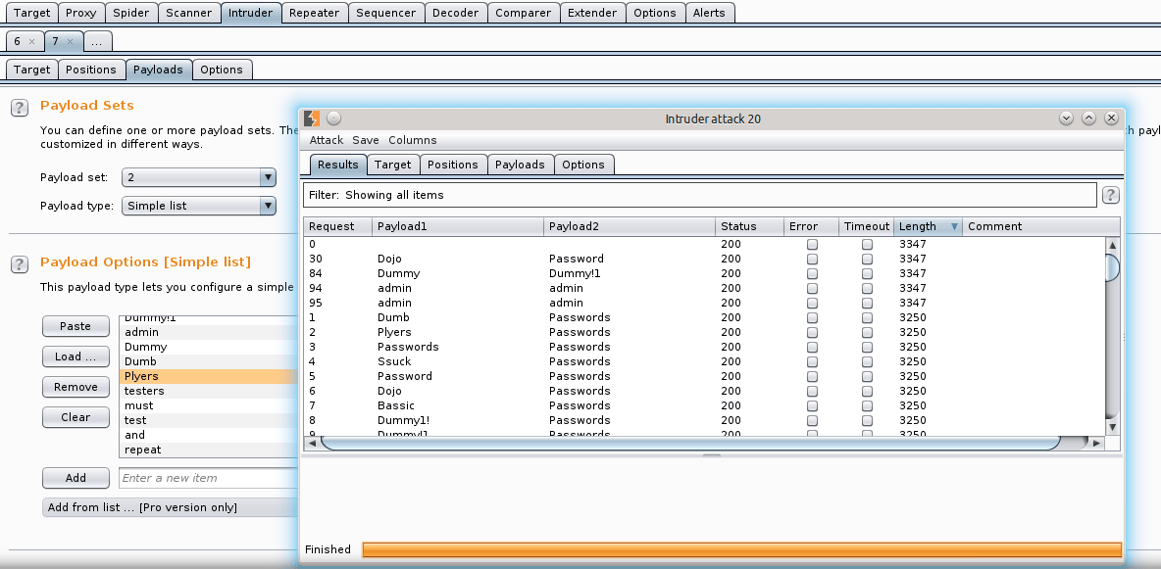
As the attack is being performed, the first request, Request 0, is the standard to which all other searches should be compared. What you will be looking for is a change in status length of the file. Using the free Burp Suite Free Edition the process is throttled down and will run very slowly.
So, we can see something interesting happening. While viewing the results as the attack is being performed, you can see that Burp is detecting passwords with logins. Again, for the purpose of testing, you want to deliberately throw in some account names and passwords that you think may have been used for this site. However, you can throw in some default passwords you find quite often like admin:admin. As you can see, Burp actually found a login credential of admin:admin during the attack. What a surprise right? Well, not exactly but we will take that as a win. Creating a good username and password cracking list is key to the success when using this tool to brute force credentials.
Taking a look even deeper we notice the lengths of the data for each attack. We noticed the Request 0, which is our standard, is 3347 bytes. Three additional account logins were discovered during the attack with the same amount of bytes. You can now send some of our target attacks to compare if you wanted to see any differences in the raw data, but feel pretty confident we have a good brute forced username and password combo. To test that these were valid accounts, you can now go back to the login page and try them out. Due to admin:admin being discovered let’s try it.
So we definitely have compromised what we believe would be the administrator’s account. There are additional things we can try while using the Intruder tab, for instance, try to capture additional user ID’s. However, this can be called a success since we have proven we can brute force a username and password and successfully use that login information to compromise the account.
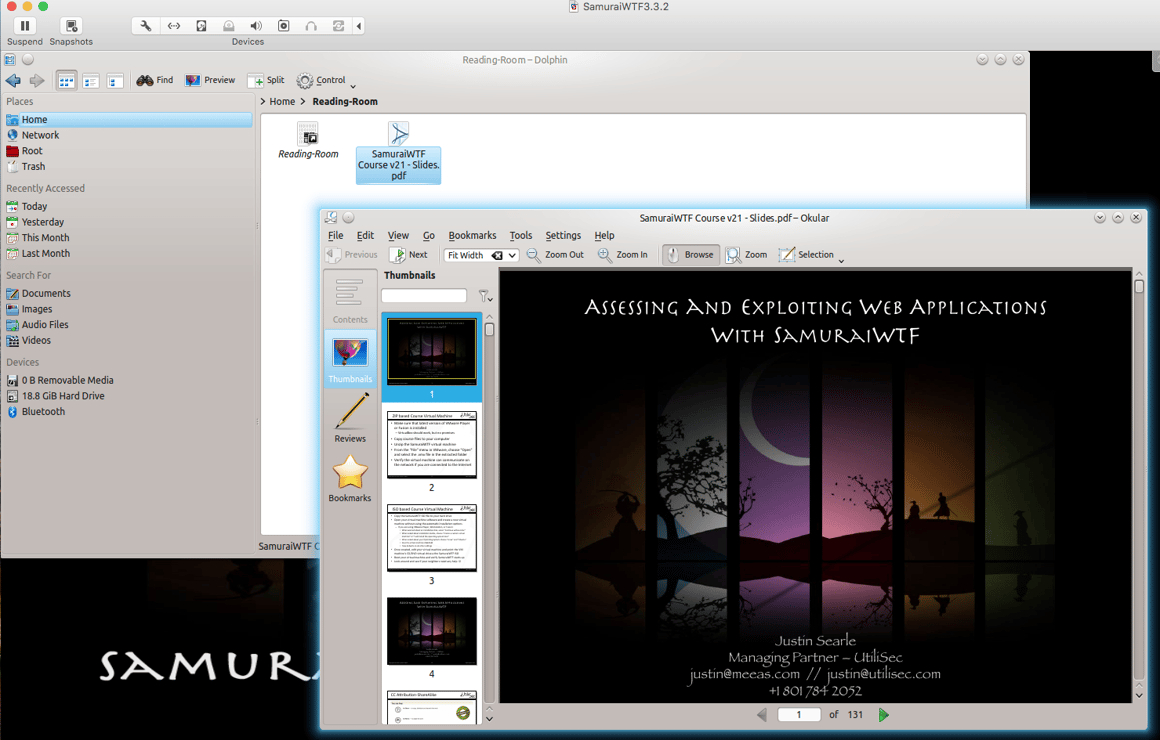
There are many useful features in the Burp Free Edition. Play around with the tools that are available to familiarize yourself with the program. I deeply recommend purchasing the full version if this is something you find useful. Also, take a look at the Samurai WTF presentation found in the Reading Room in the Home directory /Reading-Room/samuraiWTFCourse v21 – Slides.pdf
Thank you for visiting the Secure Ideas Blog on using Burp and stay tuned for additional blogs that will feature additional tools.