Welcome to the 5th blog on Burp Suite, and Happy 4th of July!
Please visit Secure Ideas’ previous blogs on using Burp Suite at the following links:
Part 1: Burp Repeater
Part 2: Introducing Burp Correlator
Part 3: Running Burp on a Mac
Part 4: Burp-suite-continuing-the-saga
As in previous articles, we will be using the virtual machine SamuraiWTF which can be found at Sourceforge.net or Github. For this blog, I will be using the dojo-scavenger website in SamuraiWTF and discussing the scanning tools that can be used in Burp.
As with any testing, whether it be on your own application or a clients, ensure a well defined scope of the testing is documented and contact any 3rd party vendors for authorization as well. With that being said, let’s dive in!
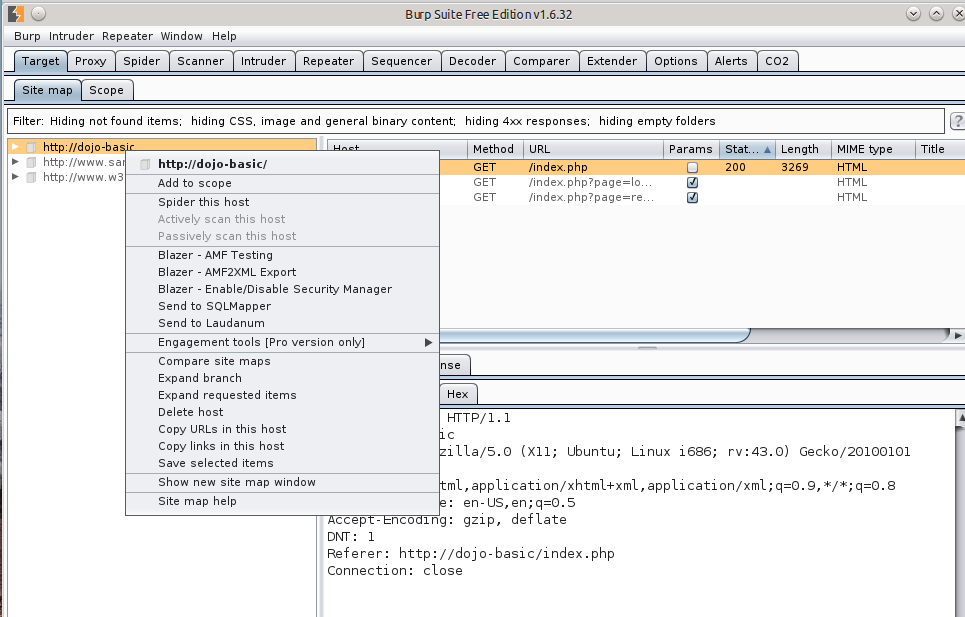
The first one I will discuss is Spider. Burp’s Spider tool can be used to automatically crawl web applications. Spider will look at resources such as form files, exposed directories, and attempt to change overall functionality of the application. One risk of using Spider as a testing tool, is that it will attempt random login requests, multiple new user account registrations, and may venture deeper than the scope of the testing allows. Having this many requests could cause a possible denial of service by locking up the web application. Due to excessive traffic and malicious login attempts the application could get overwhelmed and not be coded to handle it. When using the Spider tool, keep this in mind and attempt only on non-production sites.
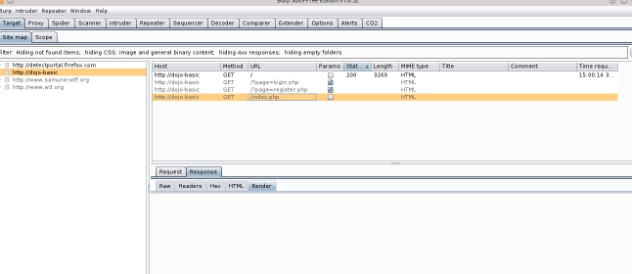
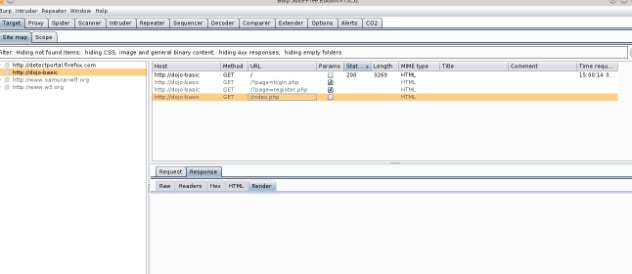
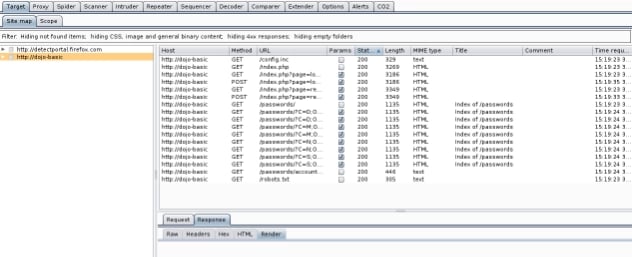
One of the benefits of this tool is that it allows mapping of an application to be performed much quicker and give you a more thorough method of mapping than if you were doing it manually. The screen capture below shows an example of the types of findings that can be exposed when using Spider vs manual mapping. These examples show results just by visiting the dojo-basic home page, no other functions were performed.
The first screenshot shows the web application details using standard mapping technique.
This second screenshot shows the results when using Spider .
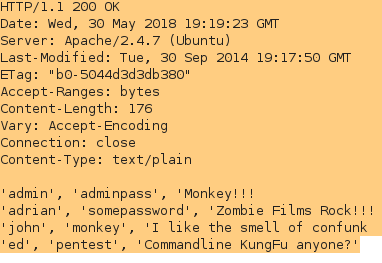
Take notice of the extra information found by using the Spider tool. There are numerous attempts at creating user accounts.
Additionally, we’ve found a file path to passwords/account directories which reveals registered users, usernames, and passwords of account users in the application.
![]()
Again, please DO NOT use this tool in a production environment and pay close attention to the scope of the testing to be performed. It is very easy to stray away from the actual target and easily crash an application’s resources.
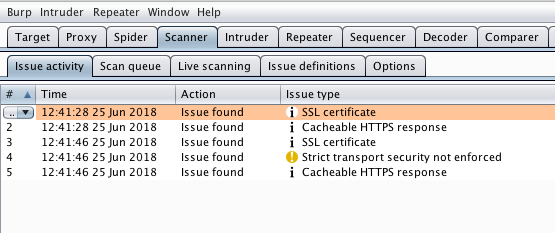
Another tool within Burp that I would like to point out is Scanner. Scanner will actually point out vulnerabilities as you go through the web application. For example, say you are mapping out a website and you want to look for common things, like missing security patches on your Apache instance. Well, if you are using the free version like I am for this blog, you won’t be able to use this tool. On the other hand if you have a valid license for Burp Pro you could select your target by simply right clicking on your transaction in the Proxy HTTP history tab and set it as in scope.
Once you have it selected as in scope, the Burp Scanner tool will do all the work. You can use Burp Scanner just like you would any other vulnerability scanner. Scanner, will actually give you real time feedback on vulnerabilities as you map out the application. This is another good reason to get a professional license!
Here is a screen capture of Scanner listing vulnerabilities found while mapping:
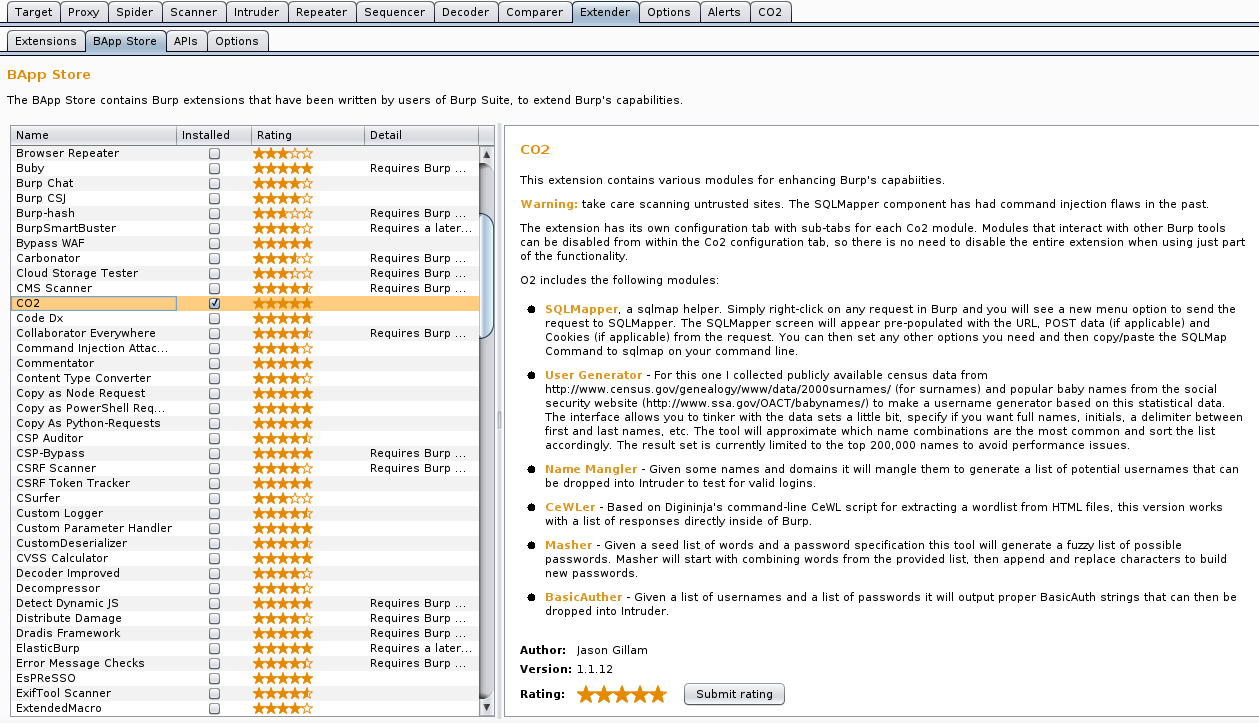
The next tab, I would like to discuss is Extender. Extender allows you to select Burp extensions like CO2, Custom Logger, and Error Message Checks. Depending on the web application testing requirements, you have additional options to incorporate plugins and extra tools to your already handy Burp software. Several of these tools require a Professional license to be used. However, there are multiple tools like CO2 that can be used with no additional purchases necessary.
Burp CO2, was created by Jason Gillam. CO2 is an extension which includes fully configurable modules that can be individually disabled based on your application testing needs.
So, I have gone through some of things you can do and some you should not do with Spider. I also discussed a little on where to find additional tools, or extensions, that can be used when testing web applications. If you did not already download Samurai WTF, I suggest checking it out. There is a great lesson guide that comes included in the VM. It can be found in the /home/samurai/Reading-Room directory of Samurai. This will greatly help out as you go through the Samurai Web Testing Framework. Stay tuned for our weekly Secure Ideas blogs, and sign up for our public Slack team by downloading Slack on you device and join professionallyevil.slack.com. You never know what you might discover!