
3 Reasons to Pentest with Brave
Penetration testing is a race against the clock. Often, we only have a few days to examine all the functionality of a web application or an API. That is why we spend a lot of time refining and modifying our pentesting workflow to shave off any inefficiencies. This process often requires a re-evaluation of the tools we bring to the task. I’m going to give you 3 reasons why you should switch to Brave as your pentesting browser.
Before we get started, I’m assuming you all know the basics on how to proxy traffic with Burp Suite, or use Foxy Proxy to route browser traffic to Burp. You should do web application pentests with Brave because…
It’s a Privacy Focused Browser
Everyone says they care about privacy, but that’s hogwash unless it’s part of the business model. The commercial web as we know it would not have been possible without advertising. Many organizations make their money through targeted advertisements. For social media giants like Google and Facebook, it is the primary revenue stream.
Brave gets its revenue from a variety of different sources. The founder of the startup raised 35 million dollars through cryptocurrency trading. Although Brave does present some advertising, none of it is custom-tailored to a user’s browsing history. The startup behind the browser is also looking into other revenue streams like an opt-in advertising program that rewards users for their time and bundling a subscription-based VPN within the browser. Unlike other web browsers, Brave is incentivized to provide services and features that enhance privacy rather than stripping it away.
It removes telemetry & third party requests
When you’re on an engagement for a production web app. You’ll get dozens, if not hundreds, of requests that are out of scope. This means that some time is wasted just filtering through traffic that is outside of the focus for a particular pentest. This is where Brave shines. It blocks known trackers and third party cookies by default. Chances are Twitter is not in scope for your engagement. If it is not in scope, then why let it clog up your Burp history with traffic.
There is another benefit that Brave offers. Unlike Firefox and Chrome, you don’t see extraneous requests constantly being vomited out of the browser. To prove this let me show you the difference between Firefox and Brave.
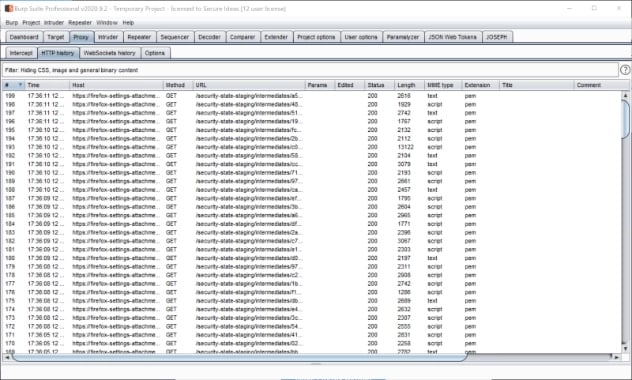
For Firefox you have more than 200 requests coming from the browser from just opening it. Now let’s compare this to Brave.
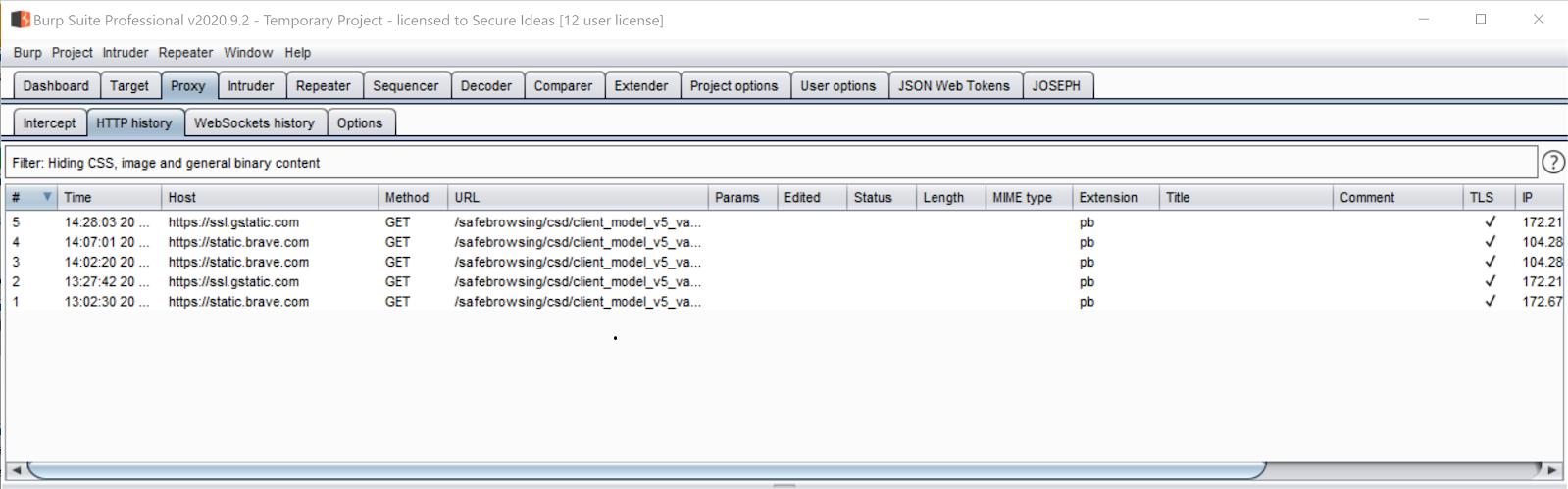
After opening it and leaving it open for two hours, Brave only sends 5 requests for static assets. That is ridiculously quiet.
Occasionally, you may need to look at out of scope traffic to see if confidential data is leaked. You can disable Brave’s blocking through the settings page on brave://settings/socialBlocking and brave://settings/shields. You can do a lot of scope filtering through Burp natively, but you do not want to drop out of scope requests. Dropping out of scope requests from Burp doesn’t just omit tracking requests. You’ll lose track of third party CDNs or a web service the client is hosting on another subdomain. The app will continue using that functionality while you test, but you won’t have visibility on it.
There is another problem with proprietary browsers: Telemetry. Browsers like Chrome, Chromium, Opera, Internet Explorer, and both versions of Microsoft Edge send system information, diagnostics, and web browsing histories to their respective owners. As pentesters, we need to take every precaution to maintain the confidentiality of customer data. By using a browser without telemetry, we can avoid data leaks.
It’s the Same But Different
People are more effective with tools that they are familiar with. For general browsing, I like Chrome on Windows and Chromium in my Linux box. The user interface just feels right to me. Everything is simple and intuitive. For pentesting, it is important to have Firefox or a Chromium-based browser because it allows me to use Foxy Proxy. This extension is one of the easiest ways to proxy browser traffic through burp. With Brave, I didn’t have to relearn how to use a different web browser or rediscover how to proxy traffic through it. It is all familiar territory since it is Chromium-based.
This is also important because some customers will optimize their web apps for usage in Chrome, so you get the privacy benefits mentioned above without running into compatibility issues.
Have I convinced you to make the switch? If not, we also have blogs on getting efficient pentesting workflows with Firefox and Internet Explorer. What’s your favorite pentesting browser? Feel free to answer in the comments section below.
If you’re interested in more advanced topics, we have an AppSec playlist on our YouTube channel that covers a variety of different areas. We also answer more fundamental questions about pentesting in our Knowledge Center. Finally, if you’re looking for a penetration test, training for your organization, or just have general security questions please Contact Us.

