How a Proactive Approach Promotes Organizational Cyber Resilience
Just a decade ago, the importance of penetration testing was not widely appreciated. Now, it is an essential component of any modern security program. The emergence of cybersecurity as a strategic priority, rather than an afterthought, has compelled organizations to adopt a far more proactive approach to countering the growing list of sophisticated cyber threats while still embracing new technologies. Whether it’s the proliferation of cloud computing or the exponential increase in internet-connected devices, these advancements have fundamentally changed how we approach penetration testing. This post aims to highlight this evolution and explain why organizations can no longer afford to be passive in their pursuit of cyber resilience.
Penetration testing, also known as pentesting, assesses existing systems, assets, and networks to uncover vulnerabilities and real-world attack vectors. However, as threat actors worldwide continue refining their techniques, security experts have responded by developing innovative solutions that build upon the foundations of standalone testing.
While Secure Ideas offers traditional penetration testing, we also recognize the need for thorough, periodic testing. As we continue to grow our services to match the evolutionary pace of our industry, we have launched a new, innovative solution: Professionally Evil Testing as a Service (PETaaS®).
To assist your organization in deciding what penetration service is right for you, our guide will explore the limitations of traditional pen test approaches, the rise of Penetration Testing as a Service (PTaaS), and how Secure Ideas’ PETaaS® takes security testing to the next level.
Whether you're a CISO, IT manager, or business leader, this comprehensive guide will equip you with the knowledge to make informed decisions about your organization's security testing strategy. Let's dive in and explore how PETaaS® is reshaping the cybersecurity landscape.
The history of penetration testing
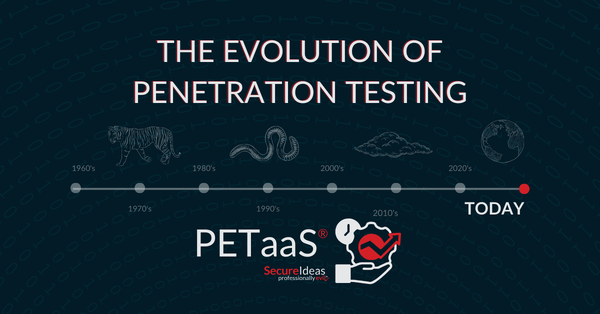
Penetration testing has roots dating back to the 1960s with the rise of computing and digital technologies. However, it gained real prominence in the 1990s as the internet became widely adopted.
Below is a timeline of the most significant developments in penetration testing and how it has transformed how we approach security tests today.
- 1960’s - 1970's: The term ‘tiger team’ was coined by NASA to describe a small team of experts working together to solve complex problems, such as those found in space missions.
- 1980’s - 1990’s: The emergence of the Morris worm in 1988, distributed via the internet, highlighted the need for security testing and resulted in the first US conviction under the 1986 Computer Fraud and Abuse Act.
- 2000's: The Open-Source Security Testing Methodology Manual (OSSTMM) was introduced as one of the first formal frameworks to guide the information technology security community in security testing at an enterprise level.
- 2000's - 2010: Compliance requirements, including PCI DSS, introduced the concept of regular security testing for organizations handling sensitive information.
- 2010's: By now, penetration testing has firmly established itself as a tool in the enterprise arsenal to handle network and internal security problems. Standalone pen tests are the most common approach, but the rise of cloud computing and mobile technologies expanded endpoints beyond the reach of internal networks, prompting more businesses than ever to consider pen testing.
- 2020's: Data breaches, ransomware, and the exploitation of zero-day vulnerabilities to hammer the defenses of organizations worldwide, including the 2021 global assault on Microsoft Exchange Servers. These security events led to the development of more continuous testing models.
- Today: Pen testing methods continue to advance. Organizations can now choose between standalone tests, periodic, or continuous models, to uncover vulnerabilities and to tackle real-world attack vectors.
This evolution has paved the way for more advanced approaches like Penetration Testing as a Service (PTaaS) and ultimately, Professionally Evil Testing as a Service (PETaaS®).
The Changing Face of Penetration Testing
Secure Ideas’ experts have observed a dramatic shift in how business leaders view cybersecurity, along with the growing importance of penetration testing.
The traditional penetration testing approach was once the gold standard of security assessments. In this approach, security consultants would conduct an assessment and provide a snapshot of an organization’s security stance and maturity level.
This involved identifying vulnerabilities, network entry points, and system weaknesses that cyber attackers could potentially exploit to infiltrate a network. A set of recommendations would follow this one-time assessment.
When it comes to penetration testing, the return on investment can be challenging to quantify as it often comes down to one statement: You haven’t been breached (at least, not yet).
We are pleased to see that the importance of security testing and the need to maintain a robust security posture is now more widely understood. However, a traditional approach to penetration testing is no longer sufficient to reach this goal.
Problems with Traditional Penetration Testing:
- Point-in-Time Assessment: Traditional pen tests provide only a snapshot of security at a specific moment.
- Problem: Vulnerabilities can emerge between annual tests, leaving organizations exposed.
- Solution: PETaaS® offers flexibility of near on-demand testing in smaller bites, ensuring infrastructure and application updates can be tested as they change.
- Limited Scope: Traditional tests often focus on predefined areas.
- Problem: This can miss emerging threats or vulnerabilities in overlooked systems.
- Solution: PETaaS® provides comprehensive coverage across your entire infrastructure, adapting to your changing environment.
- Inflexible Engagement: Traditional pen tests are often scoped as a single monolithic exercise.
- Problem: Traditional pen tests are often behind schedule before they even make it through procurement. Most organizations find it impractical to change or add scope once the contract is signed.
- Solution: PETaaS® offers real flexibility by working as a single trip through procurement to perform multiple assessments.
- Lack of Context: Traditional reports may not account for an organization's specific risk profile.
- Problem: This can lead to misallocated resources and ineffective remediation efforts.
- Solution: PETaaS® provides contextualized insights, tailoring recommendations to your unique environment and risk tolerance. Knowledge gained from one assessment is leveraged in following assessments.
- Resource Intensive: Coordinating and preparing for annual pen tests can be time-consuming and disruptive.
- Problem: This can lead to resistance to frequent testing, potentially leaving vulnerabilities undetected.
- Solution: PETaaS® integrates seamlessly into your existing processes, minimizing disruption while maximizing security insights.
|
Traditional Pen Testing |
PETaaS® |
|
One-time assessment |
Continuous, ongoing testing |
|
Static snapshot of security posture |
Dynamic, real-time security insights |
|
Limited to scheduled intervals |
On-demand testing and periodic updates |
|
Basic vulnerability identification |
Comprehensive attack simulations and support |
Security Testing: A Core Business Process
“More and more of the organizations we work with are moving toward a model where security testing is just becoming a business process. They understand they have to do it, and they care about doing it.” - Kevin Johnson, Secure Ideas CEO
Businesses today face an unprecedented array of cyber threats. Ransomware, malware, phishing, and exploitable vulnerabilities can all lead to surveillance, network infiltration, intellectual property theft, and data breaches – any of which can be disastrous for organizations of any size.
For instance, the 2024 Verizon DBIR reports that ransomware and extortion breaches have a median loss of $46,000, with potential losses ranging up to $1.14 million. Additionally, the median time for users to fall for phishing emails is less than 60 seconds, highlighting the urgency of effective security measures. In addition, IBM’s 2024 Cost of a Data Breach report estimates that the global average cost of a data breach is now $4.88 million, a 10% increase year-over-year and the highest amount to date.
These examples underscore the critical need for continuous security testing to identify these gaps in security and mitigate risks effectively.
Security testing is no longer optional. Instead, it is becoming integral to modern operations and is increasingly recognized by business leaders as a core business process and required under a variety of regulations including PCI DSS and DORA.
Now that security testing is widely sought after, many organizations have adopted this new model of continuous penetration testing.
However, “Penetration Testing as a Service” is a blanket term encompassing various beneficial services: continuous penetration testing, on-demand testing, and security audits integrated within the software development life cycle (SDLC). As with traditional tests, PTaaS services should also include reports and recommendations.
Despite the obvious benefits of PTaaS offerings, they sometimes fall short. In some cases, PTaaS may only mean automated vulnerability scanning, and may lack the comprehensive support, communication, insights, and scalability that enterprise organizations require today. Given the diverse interpretations of continuous penetration testing, our goal is to guide you in asking the proper questions to identify the best testing solution for your organization's requirements.
Why a Proactive Approach to Cybersecurity Safeguards Your Business
Frequent security testing benefits security programs of all maturity levels. Businesses can no longer afford to rely on a reactive approach to cybersecurity and security incidents; instead, a proactive stance is essential.
To truly be proactive, expert-led security testing is crucial and demonstrates to customers and shareholders that an organization is taking security and data protection seriously.
Penetration testing can uncover vulnerabilities and provide a clear picture of an organization’s security posture. Armed with this information, companies can significantly reduce the risk of data breaches or security events, reduce their attack surface, and obtain the insight and understanding necessary to develop effective security policies and incident response plans.
Moreover, granted a deep understanding of their security posture through penetration testing, organizations can prioritize resource allocation and investments focusing on the vectors and risks most likely to impact them.
Partnering with the right security testing provider catalyzes a chain of business benefits. By transforming security testing from a periodic checkbox to an ongoing strategic process, organizations unlock multiple advantages. They not only meet and exceed regulatory requirements but also position themselves as security-conscious leaders in their field.
This reputation for robust data protection resonates with customers and partners alike, fostering trust and loyalty. In an era where a single breach can tarnish a brand, a proactive security stance becomes a compelling competitive advantage and a cornerstone of business resilience.
PETaaS®: Revolutionizing Penetration Testing with a Professionally Evil Approach
The emergence of PTaaS services underscored the growing need for continuous security testing. As cyber threats and attacker tactics, techniques, and procedures (TTPs) continue to evolve, penetration testing solutions must adapt accordingly.
In response, Secure Ideas has launched its own version of PTaaS that raises the security bar, Professionally Evil Testing as a Service (PETaaS®).
PETaaS® delivers exceptional value and a return on investment far beyond the confines of a traditional pen test. Through PETaaS®, we act as an extension of your IT team and become a true partner for innovative security testing.
We offer unparalleled flexibility in scheduling, allowing you to prioritize testing needs as they evolve. Our approach helps identify the most critical risks at any given moment, ensuring resources are focused where they matter most.
Beyond testing, we provide ongoing advisory support throughout your product development cycles and offer valuable insights to internal red teams. This continuous collaboration empowers your organization to maintain a robust security posture in an ever-changing threat landscape.
“We aim to provide a dependable, scalable, and continuous penetration testing partner for businesses of all sizes. PETaaS® will revolutionize the way organizations approach information security assessments and ensure they remain aware of ever-evolving cyber threats." - Kevin Johnson, CEO of Secure Ideas
But why "Professionally Evil"? Our experts embody the mindset of real-world attackers, simulating advanced threat scenarios to thoroughly assess your systems. We identify vulnerabilities through the lens of a potential adversary, uncovering realistic exploitation paths that traditional testing might miss. Sometimes you have to think like a criminal in order to solve the crime, and we do just that…but with permission.
Why Secure Ideas’ PETaaS® Redefines Pen Testing Benchmarks
We’re committed to helping you identify and prioritize the risks and vulnerabilities that matter the most, not just perform a fancy exploit. By partnering with Secure Ideas, you gain a team that combines attacker ingenuity with unwavering professional ethics.
This approach delivers exceptional value and ROI, surpassing traditional penetration testing and arming you with the information and support to actually move the security needle in a direction that matters.
By combining manual testing efforts with automated testing tools and techniques, our innovative approach sets us apart and is the cornerstone of our company: the belief that the “human touch” is crucial for helping our clients truly tackle today’s risks.
The Value of the 'Human Touch':
- Expert Insights: Our experts frequently identify threats that automated tools miss.
- Continuous Learning: Our team stays ahead of evolving threats through continuous education and adaptation.
- Customized Approach: Secure Ideas offers a bespoke penetration testing experience specific to your organization's infrastructure and processes, providing expert advice and targeted insights that generic testing may miss.
Our industry is evolving, and through that evolution, standalone penetration tests are no longer enough. Through PETaaS®, Secure Ideas is dedicated to providing reliable, scalable security testing services that highlight real-world risk factors and advises you on what matters the most.
Want to learn more about Professionally Evil Testing as a Service (PETaaS®)? If you wish to discuss your security testing needs, talk with an expert today.