- We have a short video on Burp in our Professionally Evil fundamentals series – https://youtu.be/vH8tEPv5AJw
- Our 2-hour Tactical Burp Suite course is now free, on YouTube – https://youtu.be/DFnxptySDgI
- Part 2 of the Postman blog series goes into detail on the Burp Suite side of the setup – /2019/03/better-api-penetration-testing-with-postman-part-2.html
- Burp Suite is available directly from PortSwigger, with a Community version available for free, which works fine for going through this process – https://portswigger.net/
1. Getting Insomnia
The main website for Insomnia is insomnia.rest, which has downloads for Windows, Mac, and Linux versions of the application. If you want to contribute to the project, or would rather get the source, you can go to their GitHub repo. It’s also available in some package managers and app stores, such as Snapcraft.io. If you’re following along, get and install Insomnia whichever way suits you.
2. Creating your first Request
Before we set up our proxy, we want to have a test request ready to verify that it’s working. Launch Insomnia, and create a new request as seen below.
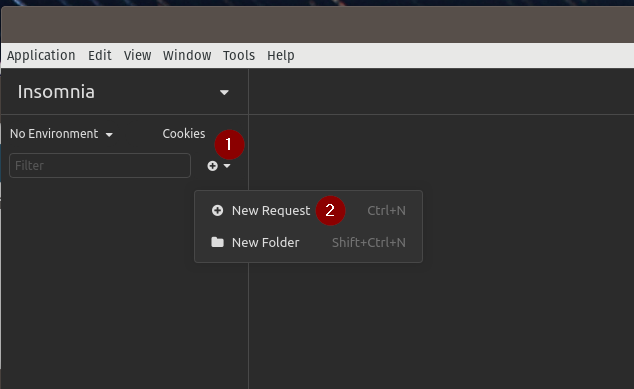
ctrl+n or click the plus with down-arrow  icon on the sidebar and select New Request.
icon on the sidebar and select New Request.Give the request a name, and click Create.
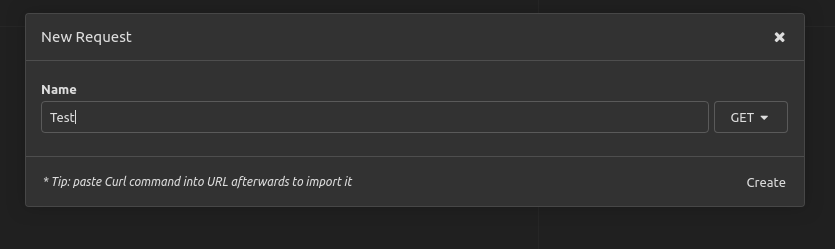
And now you need a valid URL. If you have an API that you’re getting ready to test, a simple request to it may do the trick. I’m going to use an unauthenticated public API with a Lorem Ipsum generator for this demonstration.
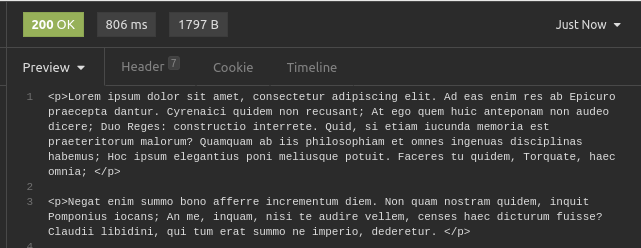
Note that it shows the HTTP response code, response time, and size. In my case, I get a chunk of Lorem Ipsum text.
3. Proxy Insomnia through Burp
I’ll assume you installed Burp Suite already. If not, then it’s available from the PortSwigger website.
Start Burp and either create a Temporary Project if you’re just trying this out, or create one on disk if you’re starting an actual test. Default Settings are fine, unless you have some custom settings you already use.
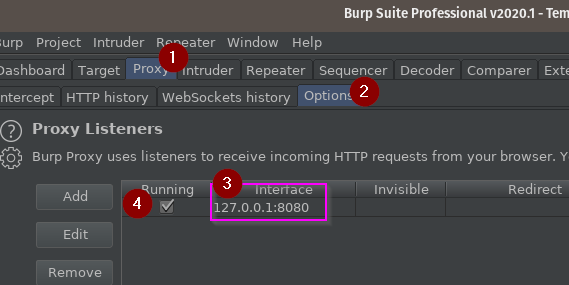
In Burp Suite:
- Go to the Proxy tab…
- …then the Options subtab.
- Note the IP and port for your proxy interface – mine is 127.0.0.1 on port 8080
- Note that the Running checkbox is checked. If this is unchecked, the default port was probably in use when you started Burp, and you can either edit the listener to change the port, or stop the application that was using it and check the box.
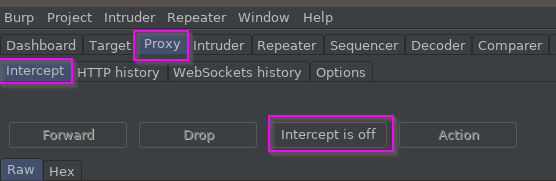
Also, go to the Intercept subtab and turn Intercept Off, unless you already have it off by default.
Insomnia natively supports proxy configurations, allowing you to simply configure the proxy settings inside of it. With Insomnia open, browse to the Application -> Preferences dialog.
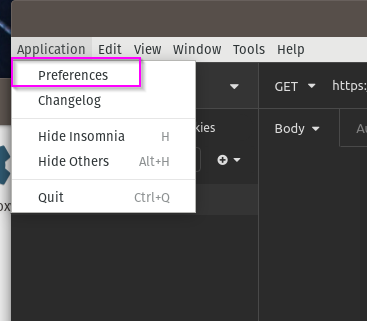
This will open a massive modal dialog full of options. The ones you care about are annotated below.
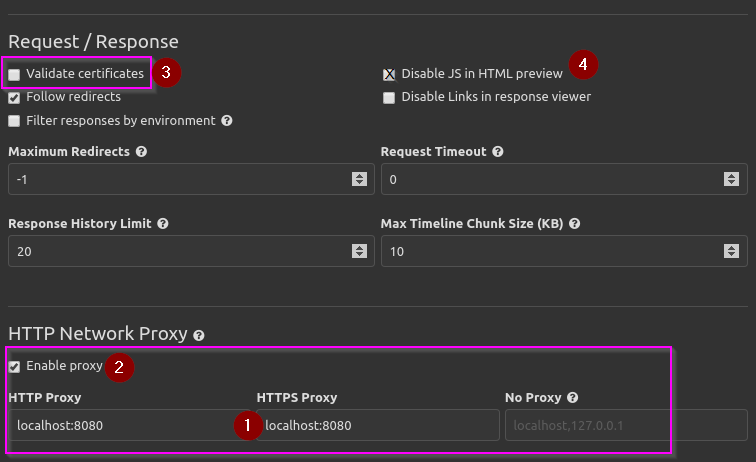
- Put your proxy interface into the HTTP Proxy and HTTPS Proxy text boxes. In my case, you see localhost, corresponding to 127.0.0.1 through my /etc/hosts file. For typical setups, this will work fine. If you have an odd setup where you’re proxying through Burp on a different machine, then the IP and port will work in the form of 192.168.10.1:8080.
- Check the box to Enable proxy, so that Insomnia proxies.
- You probably want to uncheck Validate certificates. This is the easiest and fastest way to prevent certificate trust issues when HTTPS traffic is proxied and re-signed with the self-signed Burp Certificate Authority (CA) from your Burp instance. If your Burp CA is trusted on your system, you may not require this step.
- You may want to think about Disabling JS in the HTML previewer. You normally won’t want or need it for testing web services.
Once these are set, run your request again and see that it completes in Insomnia and shows up in Burp. I usually look under Proxy -> HTTP History.
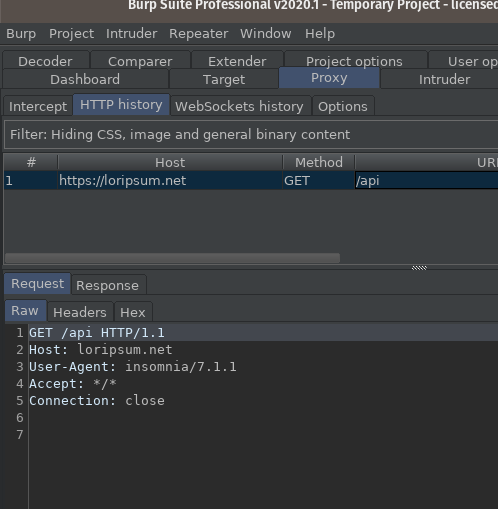
If you’re not getting a response, retrace back through the steps again and check that your Proxy Listener is listening, your host and port are correct in both applications, and Intercept is off in Burp.
Once it’s all working together, you can use Insomnia as your clean-state client for API requests. This allows you to take advantage of Repeater and Intruder for tampering and fuzzing in Burp, respectively, along with it’s extensive security-oriented plugin ecosystem.
Further Reading
If you’re coming from Postman and are used to scripting the ability to pick-up bearer tokens and set them to environment variables, you may want to look at Insomnia’s Request Chaining documentation, which is how they currently approach that problem: https://support.insomnia.rest/article/43-chaining-requests
Part 4 of the Better API Penetration Testing with Postman blog series deals with Burp plugins I like for API testing. These are just as applicable with Insomnia.
